HP StorageWorks 2/16V Brocade Fabric Watch Administrator's Guide - Supporting - Page 25
TABLE 7, Secure Fabric OS Administrator's Guide
 |
View all HP StorageWorks 2/16V manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 25 highlights
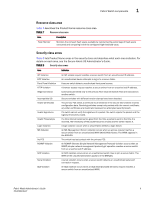
Fabric Watch components 1 Resource class area Table 7 describes the Product Name resource class area. TABLE 7 Resource class area Area Description Flash Monitor Monitors the compact flash space available by calculating the percentage of flash space consumed and comparing it with the configured high threshold value. Security class areas Table 8 lists Product Name areas in the security class and describes what each area indicates. For details on each area, see the Secure Fabric OS Administrator's Guide. TABLE 8 Security class areas Area Indicates API Violation DCC Violation Front Panel Violation HTTP Violation Illegal Command Incompatible DB Invalid Certificates Invalid Signatures Invalid Timestamps Login Violation MS Violation No FCS RSNMP Violation SCC Violation Serial Violation SES Violation An API access request reaches a secure switch from an unauthorized IP address. An unauthorized device attempts to log in to a secure fabric. A secure switch detects unauthorized front panel access. A browser access request reaches a secure switch from an unauthorized IP address. Commands permitted only to the primary Fibre Channel Switch (FCS) are executed on another switch. Secure switches with different version stamps have been detected. The primary FCS sends a certificate to all switches in the secure fabric before it sends configuration data. Receiving switches accept only packets with the correct certificate; any other certificates are invalid and represent an attempted security breach. If a switch cannot verify the signature of a packet, the switch rejects the packet and the signature becomes invalid. If a time interval becomes too great from the time a packet is sent to the time it is received, the timestamp of the packet becomes invalid and the switch rejects it. A login violation occurs when a secure fabric detects a login failure. An MS (Management Server) violation occurs when an access request reaches a secure switch from an unauthorized WWN (World Wide Name). The WWN appears in the ERRLOG. The switch has lost contact with the primary FCS. An RSNMP (Remote Simple Network Management Protocol) violation occurs when an SNMP (simple network management protocol) get operation reaches a secure switch from an unauthorized IP address. An SCC violation occurs when an unauthorized switch tries to join a secure fabric. The WWN of the unauthorized switch appears in the ERRLOG. A serial violation occurs when a secure switch detects an unauthorized serial port connection request. An SES violation occurs when an SES (SCSI Enclosed Services) request reaches a secure switch from an unauthorized WWN. Fabric Watch Administrator's Guide 9 53-0000438-01