McAfee PASCDE-AB-IA Product Guide - Page 13
Use of ePolicy Orchestrator software features
 |
View all McAfee PASCDE-AB-IA manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 13 highlights
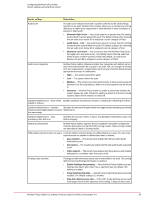
Getting started with McAfee Policy Auditor Use of ePolicy Orchestrator software features Installing the agent plug-in adds a product icon to the McAfee Agent system tray. In Windows environments, the product icon optionally displays a balloon tip to indicate the system is being audited. Systems that have the McAfee Policy Auditor agent plug-in installed are known, in McAfee Policy Auditor terminology, as managed systems. Use of ePolicy Orchestrator software features McAfee Policy Auditor is an extension of ePolicy Orchestrator software, and uses and relies upon many of its features. McAfee Policy Auditor is configured from the ePolicy Orchestrator server. The ePolicy Orchestrator server is the center of your managed environment and provides a single location where you can administer and monitor security settings throughout your network. You can use the default settings or configure the settings to match your organizational needs. This table lists the applicable ePolicy Orchestrator software features and describes how they are used by McAfee Policy Auditor. You should become familiar with each of the listed features and their uses. ePolicy Orchestrator feature Assign Policies Client tasks Location Used by McAfee Policy Auditor Menu | Systems | To assign policies, like file integrity System Tree | Assigned monitor, to managed systems. Policies Menu | Systems | System Tree | Client Tasks • To deploy the McAfee Policy Auditor agent plug-in to detected systems. • To update the McAfee Policy Auditor agent plug-into the latest version. • To wake up the McAfee Agent on selected systems. Contacts Dashboards and Monitors Menu | User To create user contact information Management | Contacts when you want to notify specific personnel by email of an event. Menu | Reporting | Dashboards • To create a new dashboard containing McAfee Policy Auditor monitors • To manage the various dashboards you use for policy audits • To access detailed information about policy audits Detected Systems (Rogue System Detection) Menu | Systems | Detected Systems • To identify systems detected by McAfee Foundstone • To determine whether the coverage of network enforcement appliances is sufficient. Issues Menu | Automation | Issues To prioritize, assign, and track issues. Issues can also be associated with tickets in a third-party ticketing server. McAfee Policy Auditor 6.0 software Product Guide for ePolicy Orchestrator 4.6 13