McAfee PASCDE-AB-IA Product Guide - Page 28
McAfee Vulnerability Manager extension integration with scannable systems, Asset Discovery scans
 |
View all McAfee PASCDE-AB-IA manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 28 highlights
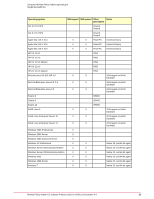
Configuring agentless audits How McAfee Policy Auditor integrates with the McAfee Vulnerability Manager extension • When you change a system from unmanaged to managed, this distinction is reflected in queries and page views. • McAfee Policy Auditor supports an all agent-based System Tree, an all agentless System Tree, and a mix of agent-based and agentless devices. A group can contain both managed and unmanaged systems. • Communication between McAfee Policy Auditor and McAfee Vulnerability Manager is through a single channel and can pass through common firewall configurations without reconfiguration. McAfee Vulnerability Manager extension integration with scannable systems The McAfee Vulnerability Manager extension can scan most operating systems supported by McAfee Policy Auditor. McAfee Vulnerability Manager can scan these operating systems: Windows 2000 Server Windows Server 2003 Enterprise Edition Windows 2000 Advanced Server Windows 2008 Server Windows 2000 Professional Solaris 8 Windows XP Professional Solaris 9 Windows Server 2003 Standard Edition Solaris 10 Windows Server 2003 Advanced Edition Red Hat Enterprise Linux 5.0, 5.1 AIX 5.3, 6.1 Asset Discovery scans ePolicy Orchestrator software supports the manual and automatic importing of systems into the System Tree. When McAfee Vulnerability Manager discovers new systems during a McAfee Vulnerability Manager Asset Discovery Scan, it designates them as rogue systems. Regardless of how assets are imported, users must add, or promote, them to the ePolicy Orchestrator server System Tree before they can be audited. McAfee Vulnerability Manager can only audit systems that have a Foundstone ID.The association between a system and a Foundstone ID is established when a system is imported from McAfee Vulnerability Manager and added to the System Tree. Data collection scans The McAfee Vulnerability Manager extension uses the Data Collection Scan to audit systems and gather compliance data. For audit results to remain current, the scan must be scheduled with sufficient time to audit systems before running the the PA: Maintain Foundstone server task. The Maintain Foundstone Audits server task The Maintain Foundstone Audits server task is responsible for setting audit frequency requirements, synchronizing audit information, distributing audit content, and performing cleanup tasks. 28 McAfee Policy Auditor 6.0 software Product Guide for ePolicy Orchestrator 4.6