McAfee PASCDE-AB-IA Product Guide - Page 42
Findings, Agentless audits, Activate benchmarks
 |
View all McAfee PASCDE-AB-IA manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 42 highlights
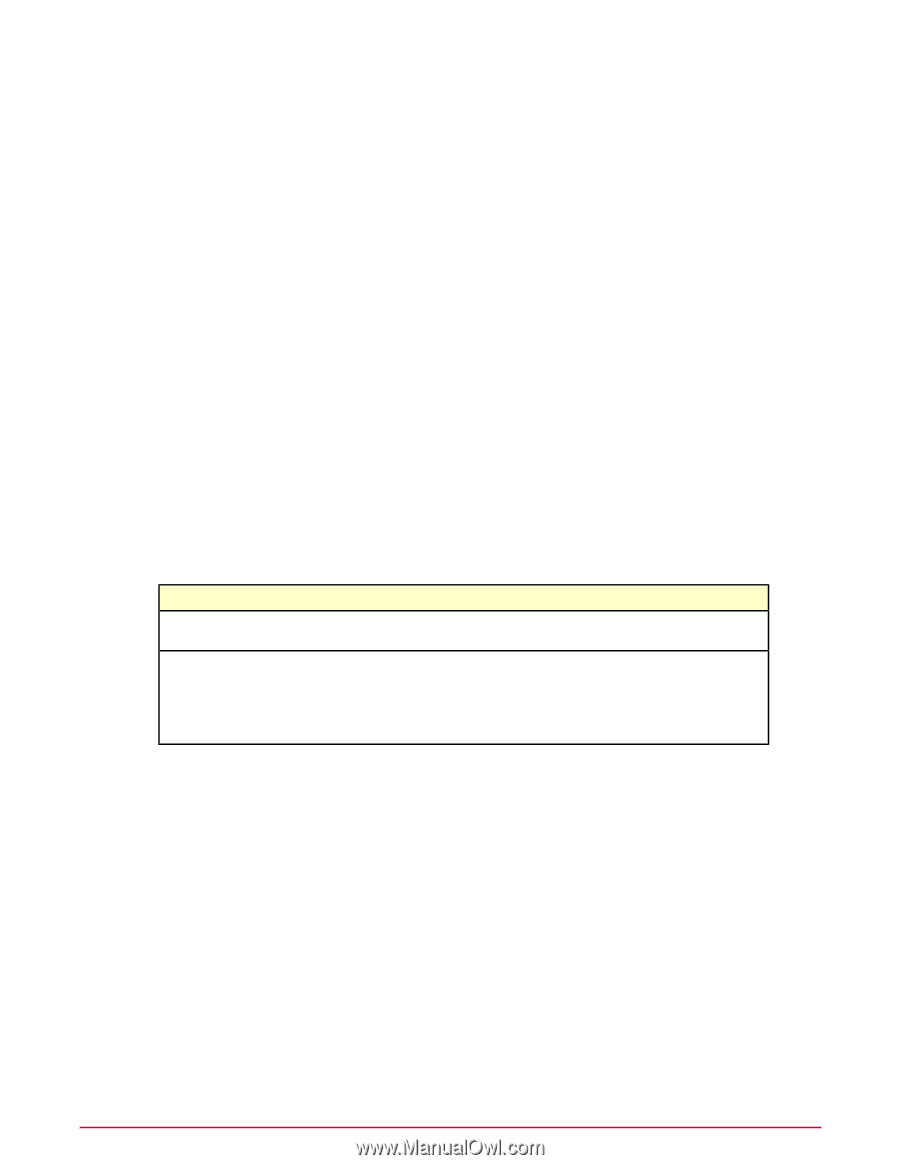
Creating and managing audits Activate benchmarks When you assign a benchmark to an audit, the benchmark selection process provides a drop-down list showing all available benchmark labels. This tool allows you to filter benchmarks based on the label that you want to use for your audit. Findings McAfee Policy Auditor provides enhanced results for checks, also known as findings. Findings results appear in monitors and queries and include additional information about the state of a system that is helpful to security officers and network administrators when fixing issues. Findings are included in reports and provide additional information in audit results. For example, if an audit expects a password with at least 8 characters but finds a password with only 6 characters, the Findings show the actual and expected results. Since it is possible to create a check that reports thousands of violations. McAfee Policy Auditor allows you to set a violation limit that reduces the number of violations that can be displayed to conserve database resources. Setting the violation limit to 0 causes monitors and queries to display all violations. Agentless audits When you create an audit, McAfee Policy Auditor provides the capability to create audits that use McAfee Vulnerability Manager (formerly Foundstone®) for some or all audits. If McAfee Policy Auditor is integrated with Foundstone, this is controlled by the Use Foundstone to audit all systems checkbox on the Properties page of the New Audit Builder. This table shows how McAfee Policy Auditor uses Foundstone to audit systems. Option Select Use Foundstone to audit all systems Deselect Use Foundstone to audit all systems Definition Uses Foundstone to conduct agentless audits of all selected systems. • Uses the McAfee Policy Auditor agent plug-in to conduct audits of systems with the plug-in. • Uses Foundstone to conduct agentless audits of systems that have been imported correctly into the System Tree. Activate benchmarks You must activate a benchmark in McAfee Benchmark Editor before you can include it in an audit. Task For option definitions, click ? in the interface. 1 Click Menu | Risk & Compliance | Benchmarks. 2 Find the benchmark to use in your audit and check its status. If the status is not active, select it and click Actions | Activate. The benchmark is activated and appears in the list of available benchmarks when you create an audit. 42 McAfee Policy Auditor 6.0 software Product Guide for ePolicy Orchestrator 4.6