McAfee PASCDE-AB-IA Product Guide - Page 74
Findings, How findings work, Types of violations
 |
View all McAfee PASCDE-AB-IA manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 74 highlights
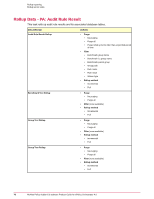
Findings Findings supplement the results of an audit check with additional information about the state of the machine. Instead of seeing a value of false for a test result, Findings give more meaningful information such as "The minimum password length is set to 6 but it should be set to 8 or higher." Contents How findings work Hide or unhide Findings results How findings work McAfee Policy Auditor reports Findings, which are enhanced results, for supported checks. Findings appear in interface pages and queries and include additional information about why a system failed a check. The software is installed as a separate extension called Findings and is exposed to McAfee and third-party applications through a Java API. This allows other applications to: • Report additional details about Findings. • Perform custom actions on Findings such as remediation on violations. • Waive or hide selected Findings. • Ignore Findings results. Findings can include three types of information: • Violations - Reporting violations provide additional information in audit results. For example, if an audit expects a password with at least 8 characters but finds a password with only 6 characters, the results show the actual and expected results. Since it is possible to create a check that reports thousands of violations. The software allows you to set a violation limit that reduces the number of violations that can be displayed to conserve database resources. Setting the violation limit to 0 causes monitors and queries to display all violations. • Compliant - A message displayed when the system complies with the audit. • Incomplete - A message displayed when the results gathered are not complete because they exceed the violation limit. Types of violations Violations are one of the types of information that can be shown by Findings. Violations can be one of three subtypes. 74 McAfee Policy Auditor 6.0 software Product Guide for ePolicy Orchestrator 4.6