McAfee PASCDE-AB-IA Product Guide - Page 14
Managed systems vs. unmanaged systems
 |
View all McAfee PASCDE-AB-IA manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 14 highlights
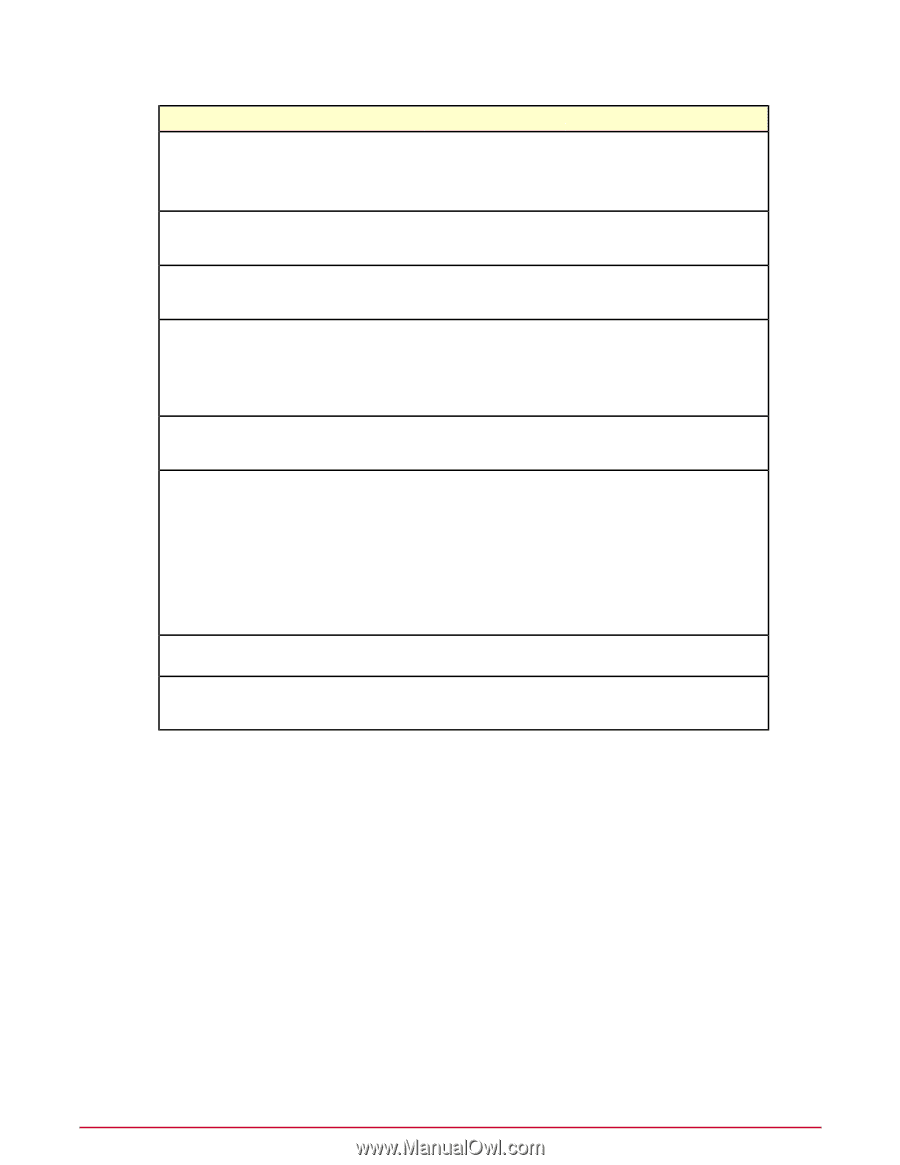
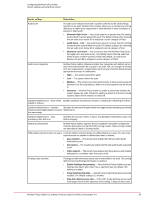
Getting started with McAfee Policy Auditor Managed systems vs. unmanaged systems ePolicy Orchestrator feature Policy Catalog Queries Registered Executables Repositories Server Settings Server Tasks Tag Catalog Users Location Menu | Policy | Policy Catalog Used by McAfee Policy Auditor • To manage the times when audits are allowed to audit systems. • To manage settings for the file integrity monitor. Menu | Reporting | Queries To create and maintain database queries regarding system security information. Menu | Configuration | To register a command that can be Registered Executables run on the server as part of an automatic response. Menu | Software | Master To check in and manage content Repository required by McAfee Policy Auditor, such as the Audit Engine content containing all the compliance and threat checks and published benchmarks. Menu | Configuration | Server Settings To specify parameter values affecting the operations of McAfee Policy Auditor. Menu | Automation | Server Tasks • To synchronize data with McAfee Vulnerability Manager using the Maintain McAfee Vulnerability Manager Audits task. • To import McAfee Vulnerability Manager data into McAfee Policy Auditor. • To manage Exemption Expiration. • To process audit results. Menu | Systems | Tag Catalog Menu | User Management | Users To create tags that can be used to help organize your systems. To create or edit a specific person as a user of McAfee Policy Auditor and their permission type. Managed systems vs. unmanaged systems Knowing how McAfee Policy Auditor classifies systems on your network is important for setting up and using the product, and for using its features. McAfee Policy Auditor uses two system classifications: Managed systems and unmanaged systems. • Managed systems - Systems in the System Tree that have both the McAfee Agent and the McAfee Policy Auditor Agent plug-in installed. • Unmanaged systems - Systems in the System Tree that do not have the McAfee Policy Auditor agent plug-in installed. These classifications, and their characteristics and requirements, apply exclusively to McAfee Policy Auditor functionality. Other McAfee products might use the same classifications, but with different characteristics or requirements. 14 McAfee Policy Auditor 6.0 software Product Guide for ePolicy Orchestrator 4.6