Lantronix SLC 32 Lantronix SLC - User Guide - Page 157
User Attributes and Permissions from LDAP Schema, LDAP Commands, RADIUS
 |
View all Lantronix SLC 32 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 157 highlights
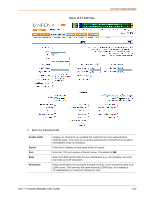
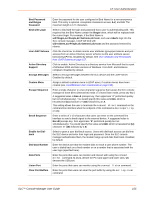
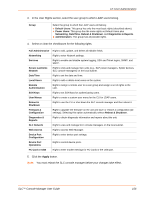
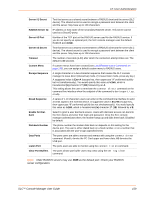
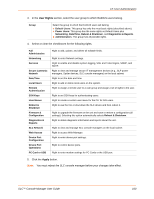
12: User Authentication User Attributes and Permissions from LDAP Schema Remote user attributes (group/permissions and port access) can be obtained from an Active Directory server schema via the user attribute secureLinxSLCPerms. This attribute is a set of parameter-value pairs. Each parameter and value is separated by a space, and a space separates each parameter-value pair. White space is not supported in the value strings. See Chapter 9: PC Cards for the parameters and values. LDAP Commands The following CLI commands correspond to the LDAP page. For more information, see Chapter 15: Command Reference . set ldap (on page 234) show ldap (on page 235) RADIUS The system administrator can configure the SLC console manager to use RADIUS to authenticate users attempting to log in using the Web, Telnet, SSH, or the console port. Users who are authenticated through RADIUS are granted device port access through the port permissions on this page. All RADIUS users are members of a group that has predefined user rights associated with it. You can add additional user rights that are not defined by the group. To configure the SLC console manager to use RADIUS to authenticate users: 1. Click the User Authentication tab and select RADIUS. Figure 12-7 shows the page that displays. SLC™ Console Manager User Guide 157