Netgear WNDAP360 WNDAP360 Reference Manual - Page 38
Security Profiles, WPA and WPA-PSK TKIP, WPA & WPA2 and WPA-PSK & WPA2-PSK mixed modes
 |
View all Netgear WNDAP360 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 38 highlights
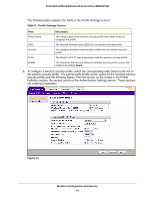
ProSafe Dual Band Wireless-N Access Point WNDAP360 • WPA and WPA-PSK (TKIP). Wi-Fi Protected Access (WPA) data encryption provides strong data security with Temporal Key Integrity Protocol (TKIP) encryption. The very strong authentication along with dynamic per frame rekeying of WPA make it virtually impossible to compromise. WPA uses RADIUS-based 802.1x authentication; for more information, see Configure and Enable Security Profiles on page 42 and Configure WPA with RADIUS, WPA2 with RADIUS, and WPA & WPA2 with RADIUS on page 49. WPA-PSK uses a pre-shared key (PSK) for authentication; for more information, see Configure and Enable Security Profiles on page 42 and Configure WPA-PSK, WPA2-PSK, and WPA-PSK & WPA2-PSK on page 50. • WPA2 and WPA2-PSK (AES). Wi-Fi Protected Access version 2 (WPA2) data encryption provides strong data security with Advanced Encryption Standard (AES) encryption. The very strong authentication along with dynamic per frame rekeying of WPA2 make it virtually impossible to compromise. WPA2 uses RADIUS-based 802.1x authentication; for more information, see Configure and Enable Security Profiles on page 42 and Configure WPA with RADIUS, WPA2 with RADIUS, and WPA & WPA2 with RADIUS on page 49. WPA2-PSK uses a pre-shared key (PSK) for authentication; for more information, see Configure and Enable Security Profiles on page 42 and Configure WPA-PSK, WPA2-PSK, and WPA-PSK & WPA2-PSK on page 50. • WPA & WPA2 and WPA-PSK & WPA2-PSK mixed modes. These modes support data encryption either with both WPA and WPA2 clients or with both WPA-PSK and WPA2-PSK clients and provide the most reliable security. WPA & WPA2 uses RADIUS-based 802.1x authentication; for more information, see Configure and Enable Security Profiles on page 42 and Configure WPA with RADIUS, WPA2 with RADIUS, and WPA & WPA2 with RADIUS on page 49. WPA-PSK & WPA2-PSK uses a pre-shared key (PSK) for authentication; for more information, see Configure and Enable Security Profiles on page 42 and Configure WPA-PSK, WPA2-PSK, and WPA-PSK & WPA2-PSK on page 50. Security Profiles Security profiles let you configure unique security settings for each SSID on each radio of the wireless access point. For each radio, the wireless access point supports up to eight security profiles (BSSIDs) that you can configure on the individual Edit Wireless Network screens that are accessible from the Edit Security Profile screen (see Configure and Enable Security Profiles on page 42). To set up a security profile, select its network authentication type, data encryption, wireless client security separation, and VLAN ID: • Network authentication The wireless access point is set by default as an open system with no authentication. Wireless Configuration and Security 38