Netgear WNDAP360 WNDAP360 Reference Manual - Page 53
Restrict Wireless Access by MAC Address, Apply, To restrict access based on MAC addresses
 |
View all Netgear WNDAP360 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 53 highlights
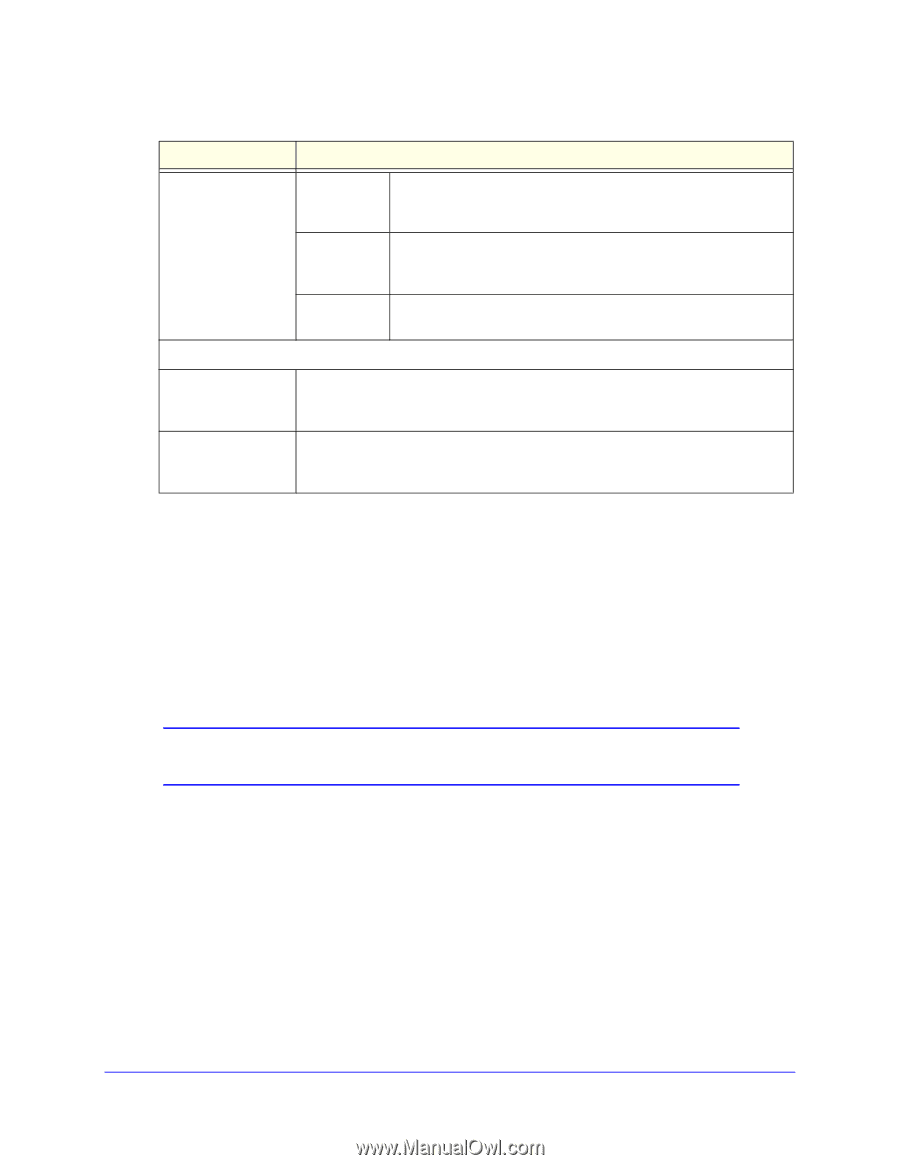
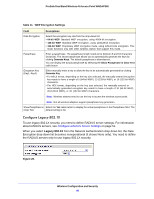
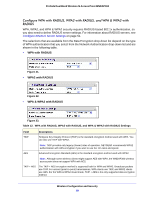
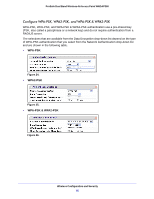
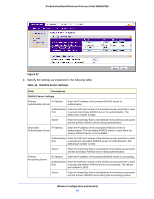
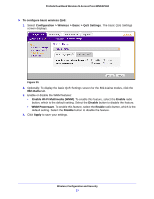
ProSafe Dual Band Wireless-N Access Point WNDAP360 Table 14. RADIUS Server Settings (Continued) Field Descriptions Secondary Accounting Server IP Address Enter the IP address of the secondary RADIUS server for accounting. The secondary RADIUS server is used when the primary RADIUS server is not available. Authentication Enter the UDP port number of the wireless access point that is used Port to access the secondary RADIUS server for accounting. The default port number is 1813. Secret Enter the shared key that is used between the wireless access point and the secondary RADIUS server during the accounting process. Authentication Settings Reauthentication Time (Seconds) The interval in seconds after which the supplicant is reauthenticated with the RADIUS server. The default interval is 3600 seconds (1 hour). Enter 0 to disable reauthentication. Update Global Key Every (Seconds) Select the check box to allow the global key update, and enter the interval in seconds. The check box is selected by default, and the default interval is 1800 seconds (30 minutes). Clear the check box to prevent the global key update. 3. Click Apply to save your settings. Restrict Wireless Access by MAC Address For increased security, you can restrict access to an SSID by allowing access to only specific computers or wireless stations based on their MAC addresses. You can restrict access to only trusted computers so that unknown computers cannot wirelessly connect to the wireless access point. MAC address filtering adds an obstacle against unwanted access to your network, but the data broadcast over the wireless link is fully exposed. Note: For wireless adapters, you can usually find the MAC address printed on the wireless adapter. To restrict access based on MAC addresses: 1. Select Configuration > Security > Advanced > MAC Authentication. The MAC Authentication screen displays. (The following figure shows one example.) Wireless Configuration and Security 53