VMware VS4-STD-C Evaluator Guide - Page 89
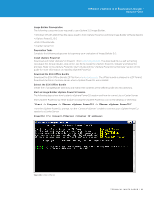
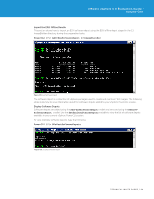
Testing SSH Firewall Rules, one of the allowed IP addresses in the firewall configuration. Therefore
 |
View all VMware VS4-STD-C manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 89 highlights
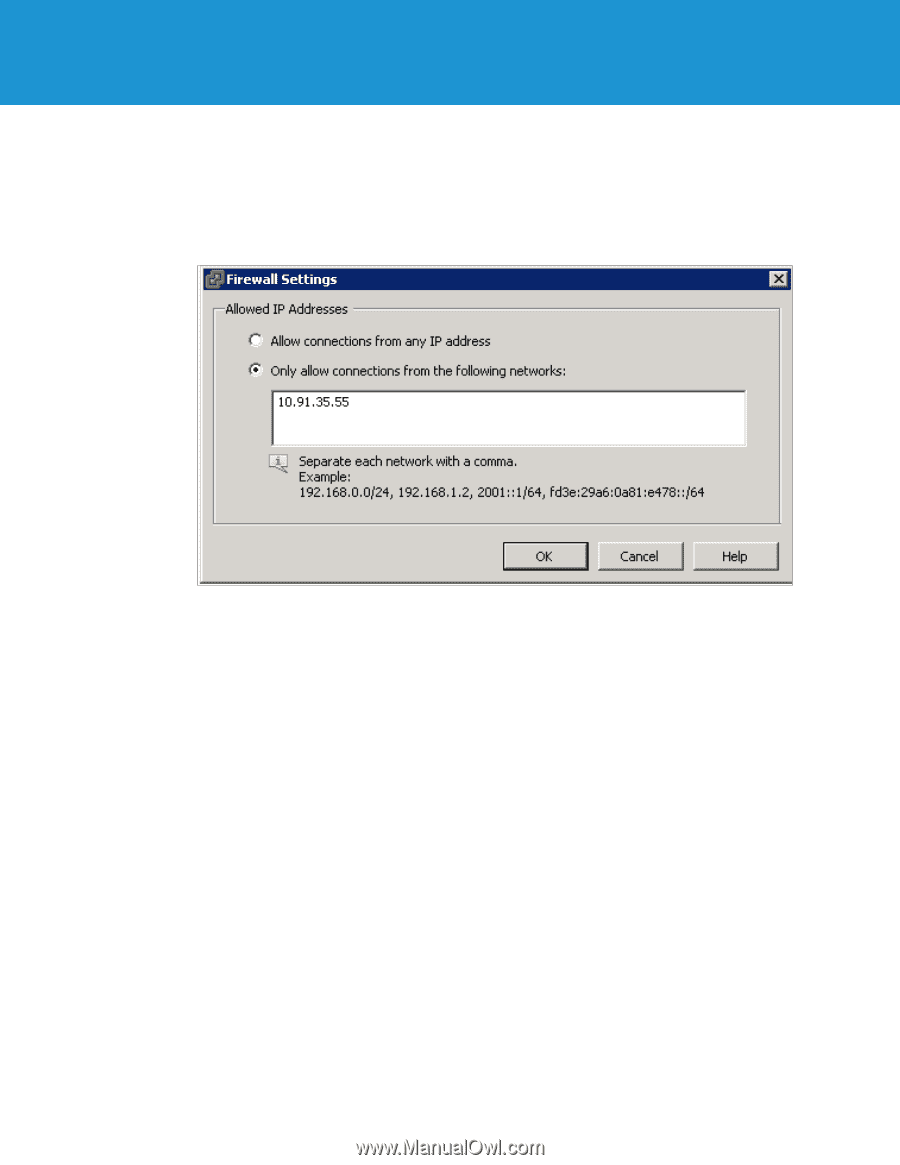
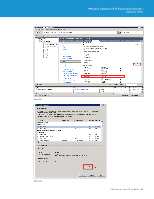
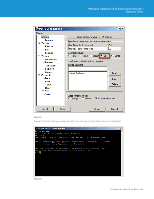
VMware vSphere 5.0 Evaluation Guide - Volume One 5. After clicking the firewall Properties link, you will see the Firewall Properties panel, as shown in Figure 120. Select the SSH Server under the Secure Shell category, and click Firewall. 6. In this example environment, you have to enable the SSH remote access only from virtual machine VM_02 with IP address 10.91.35.55. SSH connections from all other IP addresses are denied. You can also give a range of IP addresses or subnet class in the "Only allow connections..." field shown in Figure 121. Figure 121. After configuring the firewall rule to allow remote access for only virtual machine VM_02, you can test this firewall setting by establishing PuTTY sessions from different virtual machines. Testing SSH Firewall Rules In this example environment, you will try to establish SSH sessions from the following two virtual machines that are running from Host3 (tm-pod01-esx03.tmsb.local): 1. VM_02 : With IP address 10.91.35.55 2. VM_04 : With IP address 10.91.35.67 First, you can try creating a SSH session using the PuTTY tool on VM_02. This virtual machine IP address is one of the allowed IP addresses in the firewall configuration. Therefore, you can expect the SSH connection to be established. TECHNICAL WHITE PAPER / 89