ZyXEL UAG715 User Guide - Page 229
Table 91, Label, Description
 |
View all ZyXEL UAG715 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 229 highlights
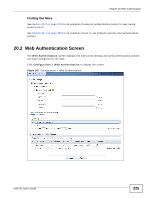
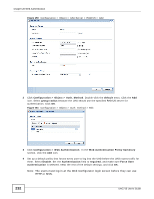
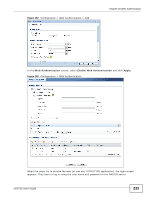
Chapter 20 Web Authentication The following table gives an overview of the objects you can configure. Table 91 Configuration > Web Authentication > Add LABEL Create new Object Enable Policy Description User Authentication Policy Source Address Destination Address Schedule Authentication DESCRIPTION Use to configure any new settings objects that you need to use in this screen. Select this check box to activate the authentication policy. This field is available for userconfigured policies. Enter a descriptive name of up to 60 printable ASCII characters for the policy. Spaces are allowed. This field is available for user-configured policies. Use this section of the screen to determine which traffic requires (or does not require) the senders to be authenticated in order to be routed. Select a source address or address group for whom this policy applies. Select any if the policy is effective for every source. This is any and not configurable for the default policy. Select a destination address or address group for whom this policy applies. Select any if the policy is effective for every destination. This is any and not configurable for the default policy. Select a schedule that defines when the policy applies. Otherwise, select none and the rule is always effective. This is none and not configurable for the default policy. Select the authentication requirement for users when their traffic matches this policy. unnecessary - Users do not need to be authenticated. Log Force User Authentication Endpoint Security (EPS) Enable EPS Checking Periodical checking time Available EPS Object / Selected EPS Object required - Users need to be authenticated. If Force User Authentication is selected, all HTTP traffic from unauthenticated users is redirected to a default or user-defined login page. Otherwise, they must manually go to the login screen. The UAG will not redirect them to the login screen. This field is available for the default policy. Select whether to have the UAG generate a log (log), log and alert (log alert) or not (no) for packets that match the default policy. See Chapter 40 on page 467 for more on logs. This field is available for user-configured policies that require authentication. Select this to have the UAG automatically display the login screen when users who have not logged in yet try to send HTTP traffic. These fields display when you set the Authentication field to required. Use these fields to make sure users' computers meet an endpoint security object's Operating System (OS) and security requirements before granting access. These fields are available for userconfigured policies that require authentication. Select this to have the UAG check that users' computers meet the Operating System (OS) and security requirements of one of the policy's selected endpoint security objects before granting access. Select this and specify a number of minutes to have the UAG repeat the endpoint security check at a regular interval. Configured endpoint security objects appear on the left. Select the endpoint security objects to use for this policy and click the right arrow button to add them to the selected list on the right. Use the [Shift] and/or [Ctrl] key to select multiple objects. Select any endpoint security objects that you want to remove from the selected list and click the left arrow button to remove them. The UAG checks authenticated users' computers against the policy's selected endpoint security objects in the order you list them here. When a user's computer matches an endpoint security object the UAG grants access and stops checking. Select an endpoint security object and use the up and down arrows to change it's position in the list. To make the endpoint security check as efficient as possible, arrange the endpoint security objects in order with the one that the most users should match first and the one that the least user's should match last. UAG715 User's Guide 229