ZyXEL UAG715 User Guide - Page 257
The VPN Connection Add/Edit IKE Screen
 |
View all ZyXEL UAG715 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 257 highlights
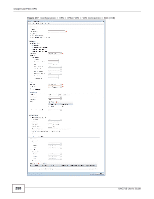
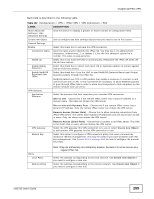
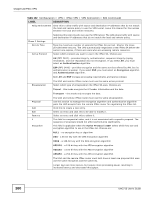
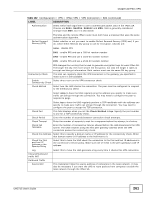
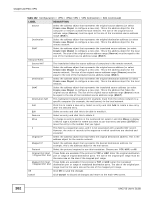
Chapter 22 IPSec VPN Each field is discussed in the following table. See Section 22.2.2 on page 263 and Section 22.2.1 on page 257 for more information. Table 101 Configuration > VPN > IPSec VPN > VPN Connection LABEL Use Policy Route to control dynamic IPSec rules DESCRIPTION Select this to be able to use policy routes to manually specify the destination addresses of dynamic IPSec rules. You must manually create these policy routes. The UAG automatically obtains source and destination addresses for dynamic IPSec rules that do not match any of the policy routes. Ignore "Don't Fragment" setting in packet header Add Edit Remove Activate Inactivate Connect Disconnect Object Reference # Status Clear this to have the UAG automatically obtain source and destination addresses for all dynamic IPSec rules. Select this to fragment packets larger than the MTU (Maximum Transmission Unit) that have the "don't" fragment" bit in the IP header turned on. When you clear this the UAG drops packets larger than the MTU that have the "don't" fragment" bit in the header turned on. Click this to create a new entry. Double-click an entry or select it and click Edit to open a screen where you can modify the entry's settings. To remove an entry, select it and click Remove. The UAG confirms you want to remove it before doing so. To turn on an entry, select it and click Activate. To turn off an entry, select it and click Inactivate. To connect an IPSec SA, select it and click Connect. To disconnect an IPSec SA, select it and click Disconnect. Select an entry and click Object Reference to open a screen that shows which settings use the entry. See Section 8.3.2 on page 115 for an example. This field is a sequential value, and it is not associated with a specific connection. The activate (light bulb) icon is lit when the entry is active and dimmed when the entry is inactive. Name VPN Gateway Encapsulation Algorithm Policy Apply Reset The connect icon is lit when the interface is connected and dimmed when it is disconnected. This field displays the name of the IPSec SA. This field displays the associated VPN gateway(s). If there is no VPN gateway, this field displays "manual key". This field displays what encapsulation the IPSec SA uses. This field displays what encryption and authentication methods, respectively, the IPSec SA uses. This field displays the local policy and the remote policy, respectively. Click Apply to save your changes back to the UAG. Click Reset to return the screen to its last-saved settings. 22.2.1 The VPN Connection Add/Edit (IKE) Screen The VPN Connection Add/Edit Gateway screen allows you to create a new VPN connection policy or edit an existing one. To access this screen, go to the Configuration > VPN Connection screen (see Section 22.2 on page 256), and click either the Add icon or an Edit icon. UAG715 User's Guide 257