ZyXEL UAG715 User Guide - Page 424
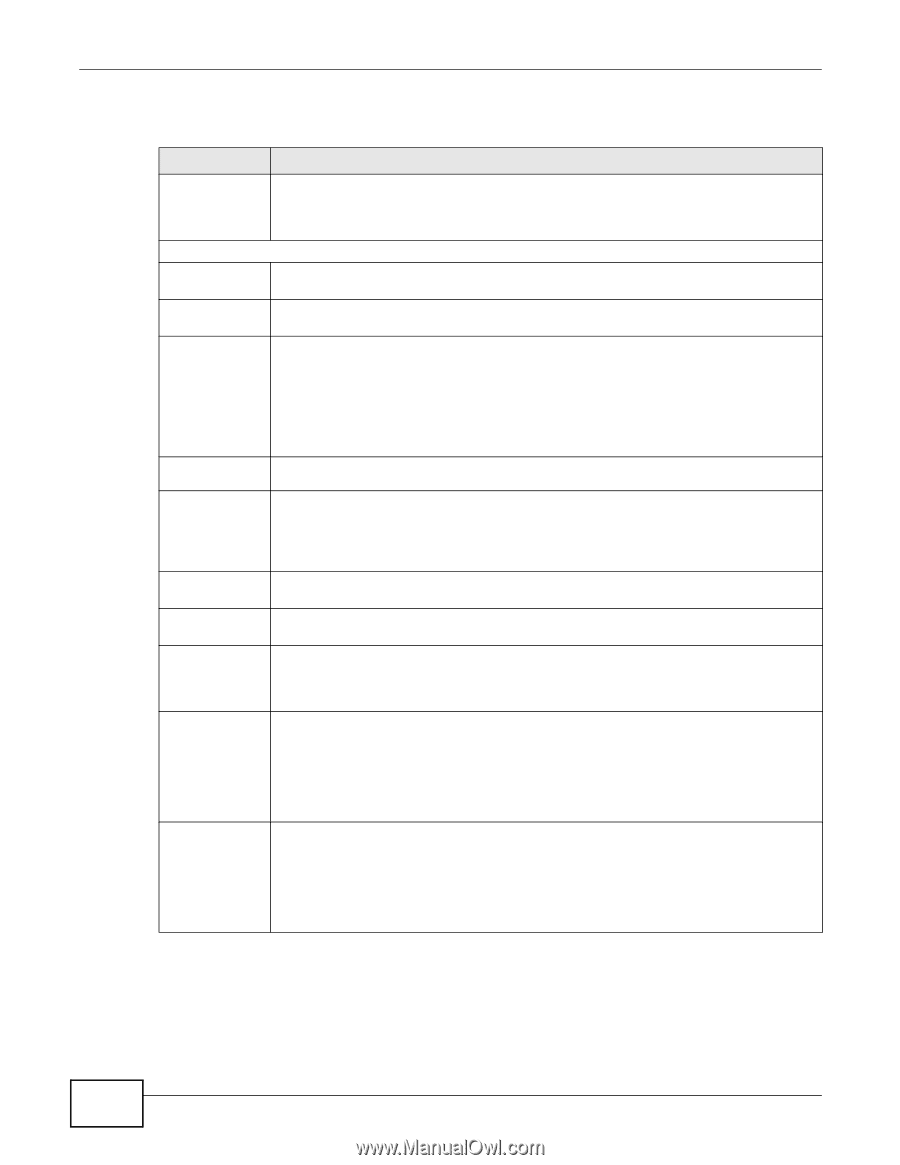
Table 170, Label, Description
 |
View all ZyXEL UAG715 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 424 highlights
Chapter 38 Endpoint Security The following table gives an overview of the objects you can configure. Table 170 Configuration > Object > Endpoint Security > Add LABEL DESCRIPTION Show Advanced Settings / Hide Advanced Settings Click this button to display a greater or lesser number of configuration fields. General Settings Object Name Specify a descriptive name for identification purposes. You can enter up to 31 characters ("0-9", "a-z", "A-Z", "-", "_" with no spaces allowed). Description Enter a description of this object. It is not used elsewhere. You can use alphanumeric and characters, and it can be up to 60 characters long. Endpoint Operating System Select the type of operating system the user's computer must be using. The checking items in the rest of the screen vary depending on the selected operating system. If you select Mac OSX, there are no other checking items. Others allows access for computers not using Windows, Linux, or Mac OSX operating systems. For example you create Windows, Linux, and Mac OSX endpoint security objects to apply to your LAN users. An "others" object allows access for LAN computers using Solaris, HP, Android, or other operating systems. Window Version If you selected Windows as the operating system, select the version of Windows here. Endpoint must update to Windows Service Pack If you selected Windows as the operating system, you can enter the minimum Windows service pack number the user's computer must have installed. The user's computer must have this service pack or higher. For example, "2" means service pack 2. Leave the field blank to have the UAG ignore the Windows service pack number. Passing Criterion Select whether the user's computer has to match just one of the endpoint security object's checking criteria or all of them. Checking Item - If you selected Windows as the operating system, you can select whether or not the user's Windows Update computer must have the Windows Auto Update feature activated. Checking Item Security Patch Use the table to list Windows security patches that the user's computer must have installed. The user's computer must have all of the listed Windows security patches installed to pass this checking item. Click Add to create a new entry. Select one or more entries and click Remove to delete it or them. Checking Item Personal Firewall If you selected Windows as the operating system, you can select whether or not the user's computer is required to have personal firewall software installed. Move the permitted personal firewalls from the Available list to the Allowed Personal Firewall List. Use the [Shift] and/or [Ctrl] key to select multiple entries. The user's computer must have one of the listed personal firewalls to pass this checking item. For some personal firewalls the UAG can also detect whether or not the firewall is activated; in those cases it must also be activated. Checking Item Anti-Virus Software If you selected Windows as the operating system, you can select whether or not the user's computer is required to have anti-virus software installed. Move the permitted anti-virus software packages from the Available list to the Allowed Anti-Virus Software List. Use the [Shift] and/or [Ctrl] key to select multiple entries. The user's computer must have one of the listed anti-virus software packages to pass this checking item. For some anti-virus software the UAG can also detect whether or not the anti-virus software is activated; in those cases it must also be activated. 424 UAG715 User's Guide