ZyXEL UAG715 User Guide - Page 332
Truncated-header Attack
 |
View all ZyXEL UAG715 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 332 highlights
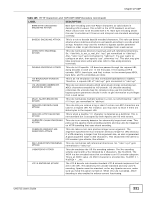
Chapter 27 ADP Table 125 HTTP Inspection and TCP/UDP/ICMP Decoders (continued) LABEL DESCRIPTION WEBROOT-DIRECTORYTRAVERSAL ATTACK This is when a directory traversal traverses past the web server root directory. This generates much fewer false positives than the directory option, because it doesn't alert on directory traversals that stay within the web server directory structure. It only alerts when the directory traversals go past the web server root directory, which is associated with certain web attacks. TCP Decoder BAD-LENGTH-OPTIONS ATTACK This is when a TCP packet is sent where the TCP option length field is not the same as what it actually is or is 0. This may cause some applications to crash. EXPERIMENTAL-OPTIONS ATTACK This is when a TCP packet is sent which contains non-RFC-complaint options. This may cause some applications to crash. OBSOLETE-OPTIONS ATTACK This is when a TCP packet is sent which contains obsolete RFC options. OVERSIZE-OFFSET ATTACK This is when a TCP packet is sent where the TCP data offset is larger than the payload. TRUNCATED-OPTIONS ATTACK This is when a TCP packet is sent which doesn't have enough data to read. This could mean the packet was truncated. TTCP-DETECTED ATTACK T/TCP provides a way of bypassing the standard three-way handshake found in TCP, thus speeding up transactions. However, this could lead to unauthorized access to the system by spoofing connections. UNDERSIZE-LEN ATTACK This is when a TCP packet is sent which has a TCP datagram length of less than 20 bytes. This may cause some applications to crash. UNDERSIZE-OFFSET ATTACK This is when a TCP packet is sent which has a TCP header length of less than 20 bytes.This may cause some applications to crash. UDP Decoder OVERSIZE-LEN ATTACK This is when a UDP packet is sent which has a UDP length field of greater than the actual packet length. This may cause some applications to crash. TRUNCATED-HEADER ATTACK This is when a UDP packet is sent which has a UDP datagram length of less the UDP header length. This may cause some applications to crash. UNDERSIZE-LEN ATTACK This is when a UDP packet is sent which has a UDP length field of less than 8 bytes. This may cause some applications to crash. ICMP Decoder TRUNCATED-ADDRESSHEADER ATTACK This is when an ICMP packet is sent which has an ICMP datagram length of less than the ICMP address header length. This may cause some applications to crash. TRUNCATED-HEADER ATTACK This is when an ICMP packet is sent which has an ICMP datagram length of less than the ICMP header length. This may cause some applications to crash. TRUNCATED-TIMESTAMPHEADER ATTACK This is when an ICMP packet is sent which has an ICMP datagram length of less than the ICMP Time Stamp header length. This may cause some applications to crash. 332 UAG715 User's Guide