HP StorageWorks 1606 Brocade Web Tools Administrator's Guide v6.3.0 (53-100134 - Page 307
Editing an IKE or IPSec policy, IPSec Protection Type
 |
View all HP StorageWorks 1606 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 307 highlights
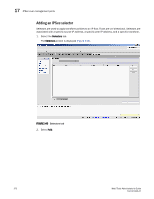
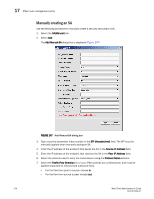
IPSec over management ports 17 8. Choose the IPSec Mode. The choices are Transport or Tunnel. Refer to"Transport mode and tunnel mode" if you are unfamiliar with Transport and Tunnel modes. 9. Choose the IPSec Protocol. The choices are ah (for authentication header) and esp (for encapsulated security protocol). 10. Choose the IPSec Protection Type. The choices are discard, bypass, or process. - Discard causes data packets to be rejected if there is an invalid pair of source and destination addresses or invalid port addresses. - Bypass allows a data packet to be transmitted or received without IPsec protection. - Process indicates a data packet is processed using IPsec encryption, IKE authentication, or both, using encapsulation security protocol (ESP) processing, or authentication header (AH) protocol processing. 11. Choose the Authentication Algorithm. The choices are hmac_md5, hmac_sha1, and AES_xcbc. 12. Type or copy a generated encryption key in the Encryption Key field. 13. Choose the Encryption Algorithm. The choices are 3des_cbc, aes_128, and aes_256. 14. Type or copy a generated authentication key in the Authentication Key field. 15. Optionally, enter a local and peer tunnel IP address. 16. Click OK. Editing an IKE or IPSec policy An existing IKE or IPSec policy can be edited. 1. Open the Switch Administration window. 2. Select Show Advanced Mode. 3. Select the Security Policies tab. 4. Under Security Policies, select Ethernet IPSec or Ethernet IPSec. 5. Select the policy you want to edit. 6. Select Edit. An Edit Policy dialog box is displayed. 7. Edit the policy as needed. 8. Click OK. Deleting an IKE or IPSec policy You can delete one or more IKE or IPSec policies. 1. Open the Switch Administration window. 2. Select Show Advanced Mode. 3. Select the Security Policies tab. 4. Under Security Policies, select Ethernet IPSec or Ethernet IPSec. Web Tools Administrator's Guide 275 53-1001343-01