HP 6125XLG R2306-HP 6125XLG Blade Switch Security Configuration Guide - Page 110
macAddressElseUserLoginSecure configuration example, Network requirements, Configuration procedure
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 110 highlights
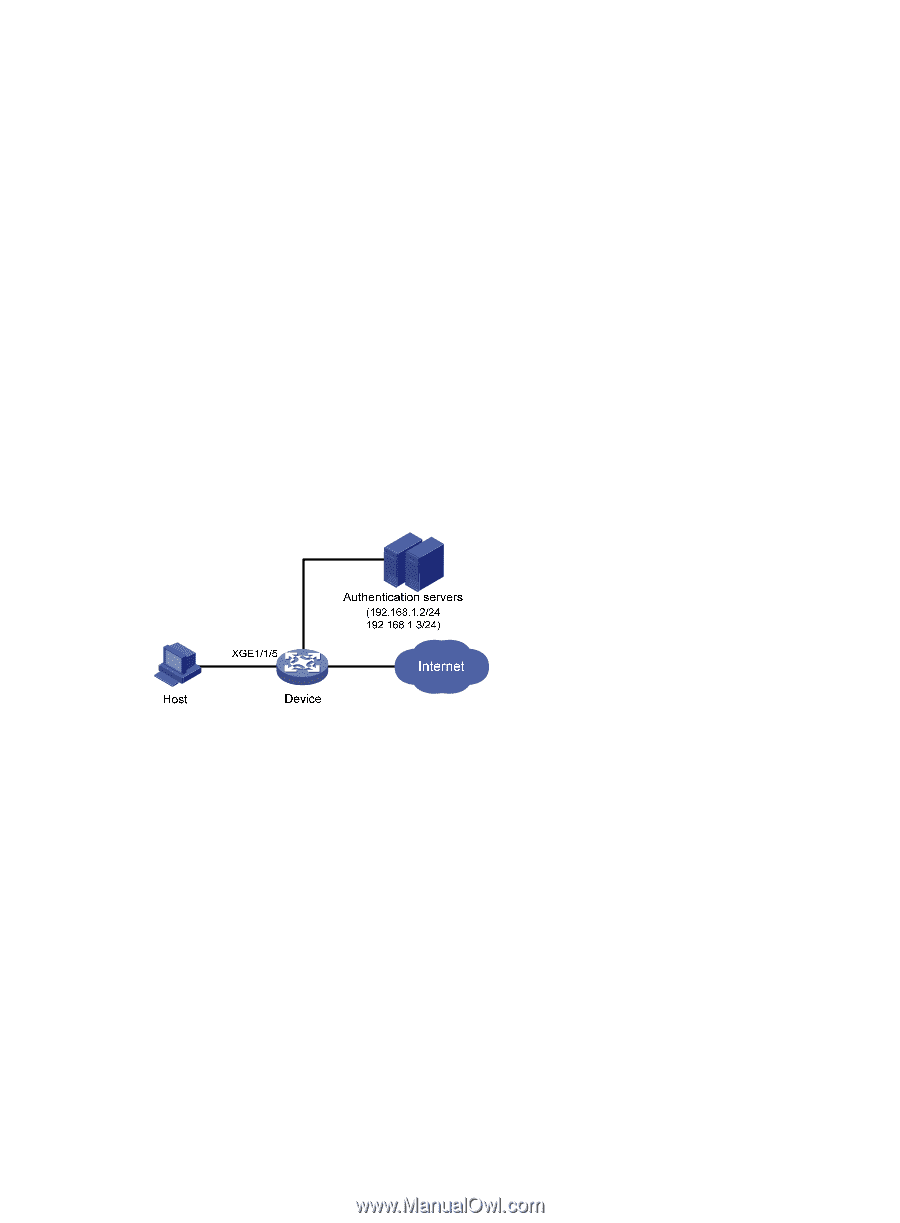
macAddressElseUserLoginSecure configuration example Network requirements As shown in Figure 37, a client is connected to the device through Ten-GigabitEthernet 1/1/5. The device authenticates the client by a RADIUS server. If the authentication succeeds, the client is authorized to access the Internet. Restrict port Ten-GigabitEthernet 1/1/5 of the device as follows: • Allow more than one MAC authenticated user to log on. • For 802.1X users, perform MAC authentication first and then, if MAC authentication fails, 802.1X authentication. Allow only one 802.1X user to log on. • Use a fixed username and password for MAC authentication of all users. • Set the total number of MAC authenticated users and 802.1X authenticated users to 64. • Enable NTK (ntkonly mode) to prevent frames from being sent to unknown MAC addresses. Figure 37 Network diagram Configuration procedure Make sure the host and the RADIUS server can reach each other. 1. Configure RADIUS authentication/accounting and ISP domain settings. (See "userLoginWithOUI configuration example.") 2. Configure port security: # Enable port security. system-view [Device] port-security enable # Configure the username and password for MAC authentication as aaa and 123456. [Device] mac-authentication user-name-format fixed account aaa password simple 123456 # Specify the MAC authentication domain. [Device] mac-authentication domain sun # Set the 802.1X authentication method to CHAP. (This configuration is optional. By default, the authentication method is CHAP for 802.1X.) [Device] dot1x authentication-method chap 101