HP 6125XLG R2306-HP 6125XLG Blade Switch Security Configuration Guide - Page 218
Configuring an IKE-based IPsec policy by referencing an IPsec policy template
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 218 highlights
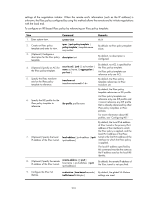
Step Command 6. Specify an IKE profile for the IPsec policy. ike-profile profile-name Remarks By default, the IPsec policy references no IKE profile, and it uses the IKE parameters configured in system view for negotiation. An IPsec policy can reference only one IKE profile and it cannot reference any IKE profile that is already referenced by other IPsec policies or IPsec policy templates. For more information about IKE profiles, see "Configuring IKE." By default, the local IPv4 address of IPsec tunnel is the primary IPv4 address of the interface to which the IPsec policy is applied, and the local IPv4 address of the IPsec 7. Specify the local IP address of local-address { ipv4-address | ipv6 tunnel is the first IPv6 address of the the IPsec tunnel. ipv6-address } interface to which the IPsec policy is applied. The local IP address specified by this command must be the same as the IP address used as the local IKE identity. 8. Specify the remote IP address remote-address { [ ipv6 ] of the IPsec tunnel. host-name | ipv4-address | ipv6 ipv6-address } By default, the remote IP address of the IPsec tunnel is not specified. 9. Set the IPsec SA lifetime. sa duration { time-based seconds | By default, the global SA lifetime is traffic-based kilobytes } used. 10. (Optional.) Set the IPsec SA idle timeout. sa idle-time seconds By default, the global SA idle timeout is used. 11. Return to system view. quit N/A 12. Set the global SA lifetime. ipsec sa global-duration { time-based seconds | traffic-based kilobytes } 13. (Optional.) Enable the global IPsec SA idle timeout function, and set the global SA idle timeout. ipsec sa idle-time seconds By default, the time-based SA lifetime is 3600 seconds, and the traffic-based SA lifetime is 1843200 kilobytes. By default, the global IPsec SA idle timeout function is disabled. Configuring an IKE-based IPsec policy by referencing an IPsec policy template The configurable parameters for an IPsec policy template are the same as those when you directly configure an IKE-based IPsec policy. The difference is that more parameters are optional for an IPsec policy template. Except the IPsec transform sets and the IKE profile, all other parameters are optional. A device referencing an IPsec policy that is configured by using an IPsec policy template cannot initiate an SA negotiation, but it can respond to a negotiation request. The parameters not defined in the template are determined by the initiator. For example, in an IPsec policy template, the ACL is optional. If you do not specify an ACL, the IPsec protection range has no limit. So the device accepts all ACL 209