HP 6125XLG R2306-HP 6125XLG Blade Switch Security Configuration Guide - Page 178
Dynamic IPv4 source guard using DHCP relay configuration example, Network requirements,
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 178 highlights
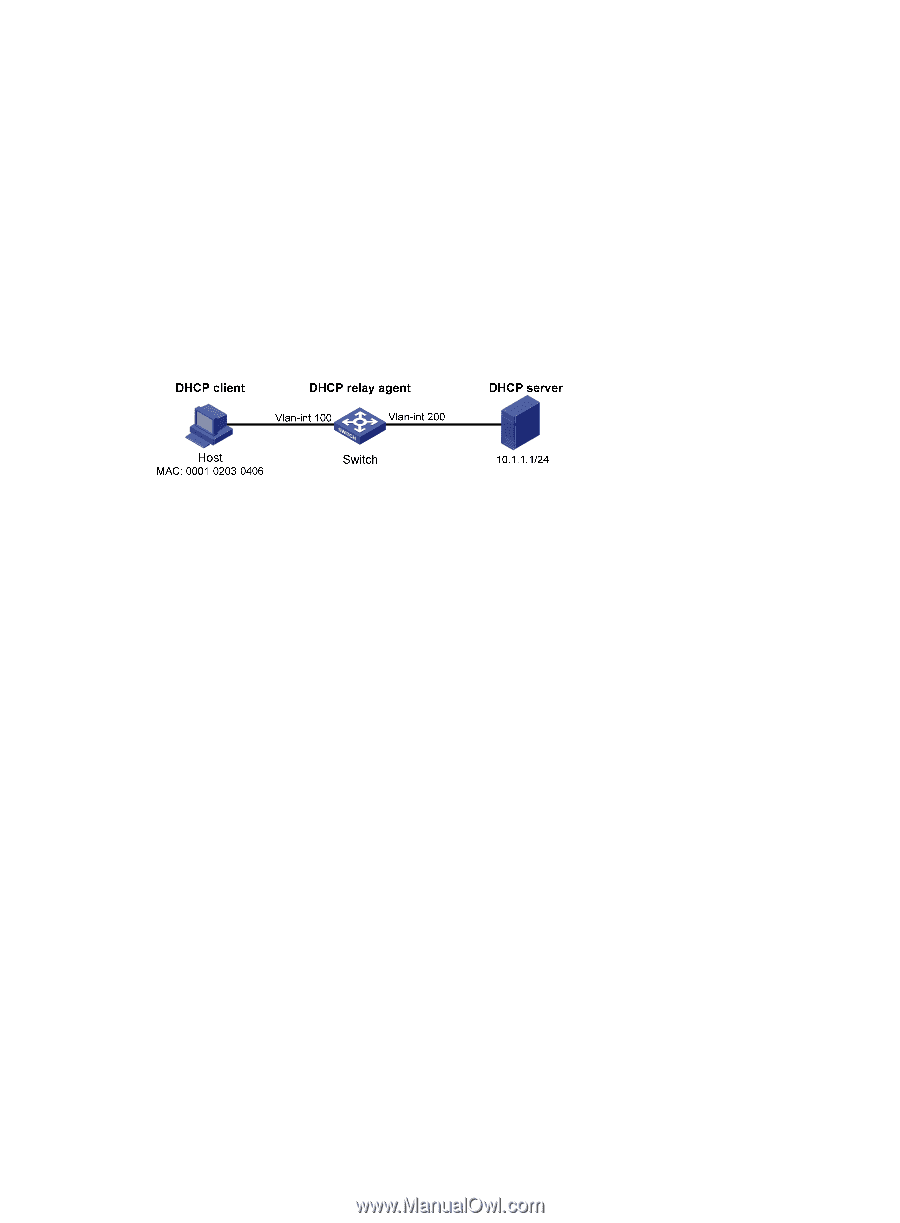
Dynamic IPv4 source guard using DHCP relay configuration example Network requirements As shown in Figure 59, the host and the DHCP server are connected to the switch through interfaces VLAN-interface 100 and VLAN-interface 200 respectively. DHCP relay is enabled on the switch. The host obtains an IP address from the DHCP server through the DHCP relay agent. Enable dynamic IPv4 source guard on VLAN-interface 100 to filter received packets based on the DHCP relay entry generated on the switch. Figure 59 Network diagram Configuration procedure 1. Configure dynamic IPv4 source guard: # Configure IP addresses for the interfaces. (Details not shown.) # Enable IPv4 source guard on VLAN-interface 100 to filter packets based on both the source IP address and the MAC address. system-view [Switch] interface vlan-interface 100 [Switch-Vlan-interface100] ip verify source ip-address mac-address [Switch-Vlan-interface100] quit 2. Configure the DHCP relay agent: # Enable the DHCP service. [Switch] dhcp enable # Enable recording DHCP relay client entries. [Switch] dhcp relay client-information record # Configure VLAN-interface 100 to work in DHCP relay mode. [Switch] interface vlan-interface 100 [Switch-Vlan-interface100] dhcp select relay # Specify the IP address of the DHCP server. [Switch-Vlan-interface100] dhcp relay server-address 10.1.1.1 [Switch-Vlan-interface100] quit Verifying the configuration # Display dynamic IPv4 source guard binding entries. [Switch] display ip source binding dhcp-relay Total entries found: 1 IP Address MAC Address Interface 192.168.0.1 0001-0203-0406 Vlan100 VLAN Type 100 DHCP relay 169