HP 6125XLG R2306-HP 6125XLG Blade Switch Security Configuration Guide - Page 96
Configuring port security, Overview, Port security features, NTK, Intrusion protection
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 96 highlights
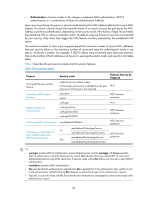
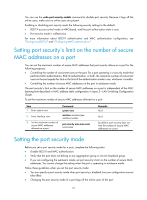
Configuring port security Overview Port security combines and extends 802.1X and MAC authentication to provide MAC-based network access control. It applies to networks, such as a WLAN, that require different authentication methods for different users on a port. Port security prevents unauthorized access to a network by checking the source MAC address of inbound traffic, and it prevents access to unauthorized devices or hosts by checking the destination MAC address of outbound traffic. Port security can control MAC address learning and authentication on a port to make sure the port learns only source trusted MAC addresses. A frame is illegal if its source MAC address cannot be learned in a port security mode or it is from a client that has failed 802.1X or MAC authentication. The port security feature automatically takes a predefined action on illegal frames. This automatic mechanism enhances network security, and reduces human intervention. NOTE: For scenarios that require only 802.1X authentication or MAC authentication, HP recommends you use the 802.1X authentication or MAC authentication feature rather than port security. For more information about 802.1X and MAC authentication, see "Configuring 802.1X" and "Configuring MAC authentication." Port security features NTK The need to know (NTK) feature prevents traffic interception by checking the destination MAC address in the outbound frames. The feature ensures that frames are sent only to hosts that have passed authentication or whose MAC addresses have been learned or configured on the access device. Intrusion protection The intrusion protection feature checks the source MAC address in inbound frames for illegal frames, and takes a predefined action on each detected illegal frame. The action can be disabling the port temporarily, disabling the port permanently, or blocking frames from the illegal MAC address for three minutes (not user configurable). Port security modes Port security supports the following categories of security modes: • MAC learning control-Includes two modes: autoLearn and secure. MAC address learning is permitted on a port in autoLearn mode and disabled in secure mode. 87