HP 6125XLG R2306-HP 6125XLG Blade Switch Security Configuration Guide - Page 190
Configuring ARP automatic scanning and fixed ARP, Configuration guidelines
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 190 highlights
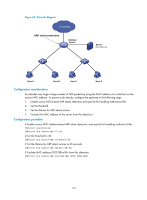
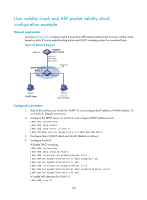
[SwitchB-vlan10] arp detection enable # Configure the upstream interface as a trusted interface (an interface is an untrusted interface by default). [SwitchB-vlan10] interface ten-gigabitethernet 1/1/7 [SwitchB-Ten-GigabitEthernet1/1/7] arp detection trust [SwitchB-Ten-GigabitEthernet1/1/7] quit # Configure a static IP source guard binding entry on interface Ten-GigabitEthernet 1/1/6 for user validity check. [SwitchB] interface ten-gigabitethernet 1/1/6 [SwitchB-Ten-GigabitEthernet1/1/6] ip source binding ip-address 10.1.1.6 mac-address 0001-0203-0607 vlan 10 [SwitchB-Ten-GigabitEthernet1/1/6] quit # Enable ARP packet validity check by checking the MAC addresses and IP addresses of ARP packets. [SwitchB] arp detection validate dst-mac ip src-mac After the configurations are completed, ARP packets received on interfaces Ten-GigabitEthernet 1/1/5 and Ten-GigabitEthernet 1/1/6 have their MAC and IP addresses checked first, and then are checked against the static IP source guard binding entries and finally DHCP snooping entries. Configuring ARP automatic scanning and fixed ARP ARP automatic scanning is usually used together with the fixed ARP feature in small-scale networks such as a cybercafe. With ARP automatic scanning enabled on an interface, the device automatically scans neighbors on the interface, sends ARP requests to the neighbors, obtains their MAC addresses, and creates dynamic ARP entries. Fixed ARP allows the device to convert existing dynamic ARP entries (including those generated through ARP automatic scanning) to static ARP entries. The fixed ARP feature prevents ARP entries from being modified by attackers. Static ARP entries can also be manually configured by the arp static command. Configuration guidelines Follow these guidelines when you configure ARP automatic scanning and fixed ARP: • IP addresses existing in ARP entries are not scanned. • ARP automatic scanning may take some time. To stop an ongoing scan, press Ctrl + C. Dynamic ARP entries are created based on ARP replies received before the scan is terminated. • The arp fixup command is a one-time operation and converts existing dynamic ARP entries to static ones. • The device has a limit on the total number of static ARP entries, including the manually configured and the converted. As a result, some dynamic ARP entries may fail the conversion. • To delete a specific static ARP entry converted from a dynamic one, use the undo arp ip-address [ vpn-instance-name ] command. Use the reset arp all command to delete all ARP entries or the reset arp static command to delete all static ARP entries. 181