HP 6125XLG R2306-HP 6125XLG Blade Switch Security Configuration Guide - Page 57
Verifying the configuration, Authentication and authorization for SSH users by a RADIUS server
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 57 highlights
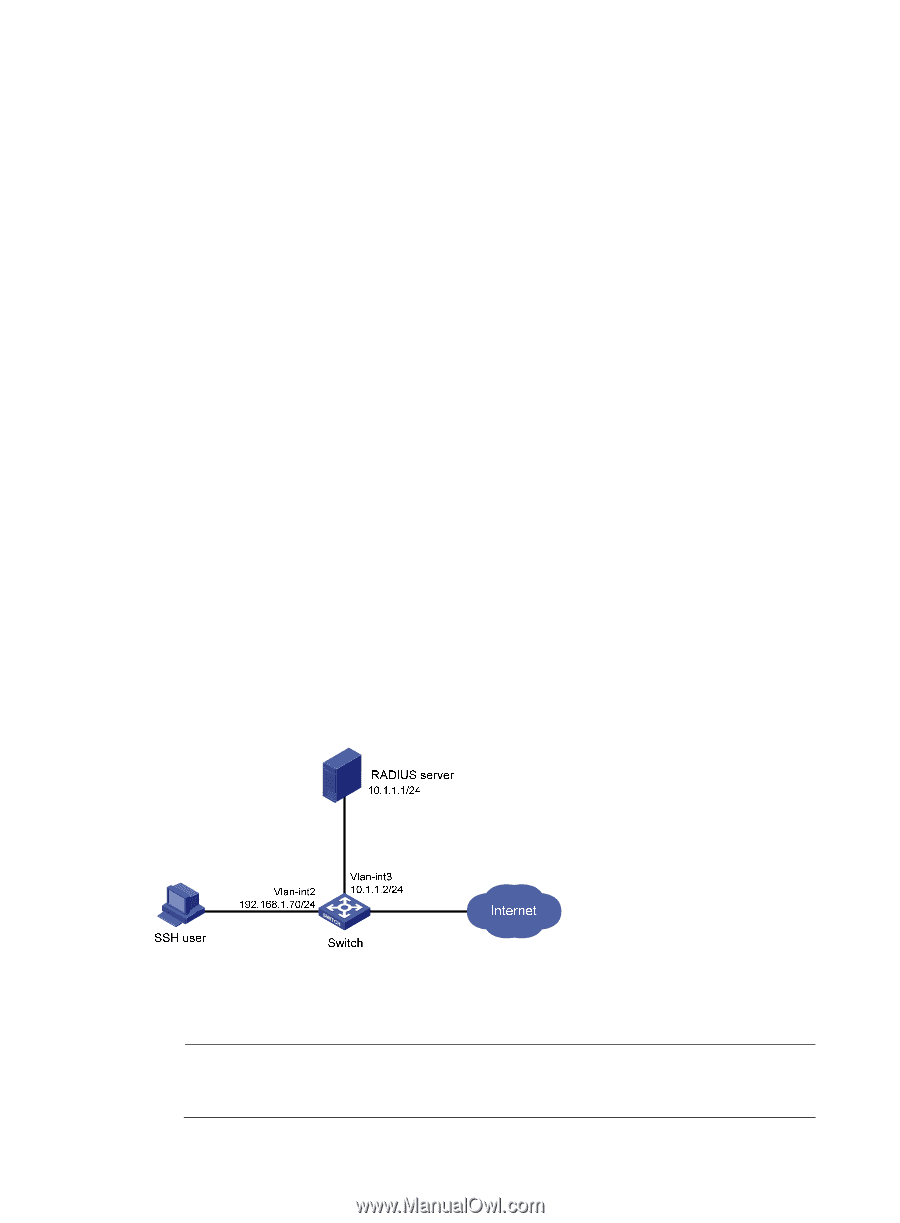
[Switch-luser-manage-hello] quit # Create ISP domain bbb and configure AAA methods for login users. [Switch] domain bbb [Switch-isp-bbb] authentication login local [Switch-isp-bbb] authorization login hwtacacs-scheme hwtac [Switch-isp-bbb] accounting login radius-scheme rd [Switch-isp-bbb] quit # Enable the default-user-role authorization function, so that an SSH user gets the default user role network-operator after passing authentication. [Switch] role default-role enable Verifying the configuration When the user initiates an SSH connection to the switch and enter the username hello@bbb and the correct password, the user successfully logs in and can use the commands for the network-operator user role. Authentication and authorization for SSH users by a RADIUS server Network requirements As shown in Figure 13, the RADIUS authentication and authorization server runs on IMC. Configure the switch to use the RADIUS server for SSH user authentication and authorization and add an account with the username hello@bbb on the RADIUS server, so that the SSH user can log in to the switch and is authorized with the network-operator user role after login. Set the shared keys for secure RADIUS communication to expert, and set the ports for authentication and accounting to 1812 and 1813, respectively. Configure the switch to include the domain name in the username sent to the RADIUS server. Figure 13 Network diagram Configuration procedure 1. Configure the RADIUS server on IMC 5.0: NOTE: This example assumes that the RADIUS server runs on IMC PLAT 5.0 (E0101) and IMC UAM 5.0 (E0101). 48