HP 6125XLG R2306-HP 6125XLG Blade Switch Security Configuration Guide - Page 20
AAA implementation on the device, User management based on ISP domains and user access types
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 20 highlights
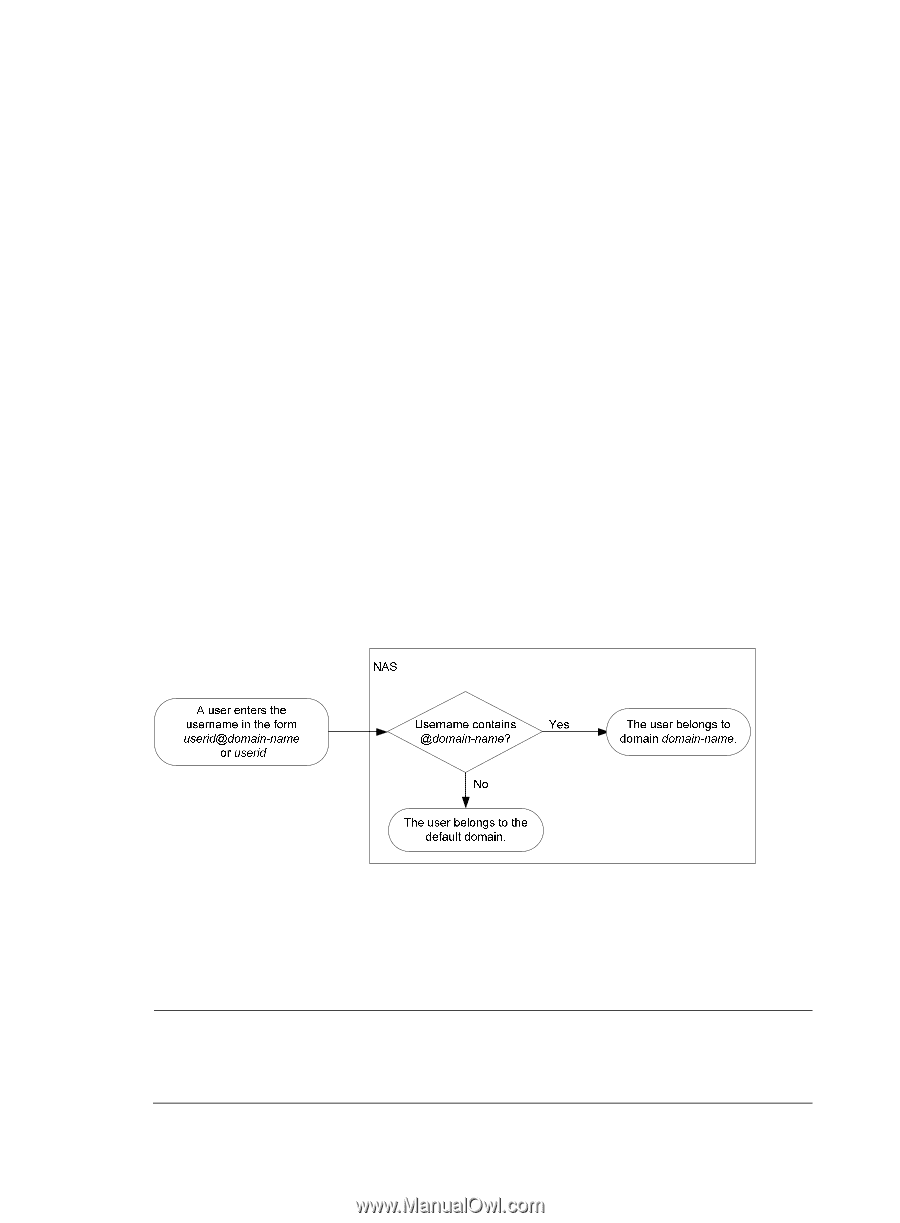
6. After receiving the request, the LDAP server searches for the user DN by the base DN, search scope, and filtering conditions. If a match is found, the LDAP server sends a response to notify the LDAP client of the successful search. There might be one or more user DNs found. 7. The LDAP client uses the obtained user DN and the entered user password as parameters to send a user DN bind request to the LDAP server, which checks whether the user password is correct. 8. The LDAP server processes the request, and sends a response to notify the LDAP client of the bind operation result. If the bind operation fails, the LDAP client uses another obtained user DN as the parameter to send a user DN bind request to the LDAP server. This process goes on until a DN is bound successfully or all DNs fail to be bound. If all user DNs fail to be bound, the LDAP client notifies the user of the login failure and denies the user's access request. 9. The LDAP client and server perform authorization exchanges. If another scheme, for example, an HWTACACS scheme, is expected for authorization, the LDAP client exchanges authorization packets with the HWTACACS authorization server instead. 10. After successful authorization, the LDAP client notifies the user of the successful login. AAA implementation on the device This section describes AAA user management and methods. User management based on ISP domains and user access types AAA manages users based on their ISP domains and access types. On a NAS, each user belongs to one ISP domain. Typically, a NAS determines the ISP domain a user belongs to by the username entered by the user at login. Figure 8 Determining the ISP domain for a user by the username AAA manages users in the same ISP domain based on their access types. The device supports the following user access types: • LAN-LAN users must pass 802.1X or MAC address authentication to get online. • Login-Login users include SSH, Telnet, FTP, and terminal users who log in to the device. Terminal users can access through a console port. NOTE: The device also provides authentication modules (such as 802.1X) for implementation of user authentication management policies. If you configure these authentication modules, the ISP domains for users of the access types depend on the configuration of the authentication modules. 11