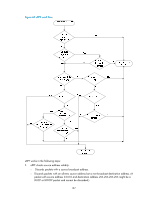
HP 6125XLG R2306-HP 6125XLG Blade Switch Security Configuration Guide - Page 200
Configuring FIPS, Overview, Configuration restrictions and guidelines
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 200 highlights
Configuring FIPS Overview Federal Information Processing Standards (FIPS), developed by the National Institute of Standard and Technology (NIST) of the United States, specify the requirements for cryptography modules. FIPS 140-2 defines four levels of security, simply named "Level 1" to "Level 4" from low to high. Currently, the switch supports Level 2. Unless otherwise specified, FIPS in the document refers to FIPS 140-2. Configuration restrictions and guidelines When you configure FIPS, follow these restrictions and guidelines: • After the fips mode enable command is executed, the system prompts you to choose a reboot method. If you do not make a choice within 30 seconds, the system uses the manual reboot method by default. • Before you reboot the device to enter FIPS mode, the system automatically removes all key pairs configured in non-FIPS mode and all FIPS-incompliant digital certificates. FIPS-incompliant digital certificates refer to the MD5-based certificates with the modulus length of key pairs less than 2048 bits. You cannot log in to the device through SSH after the device enters FIPS mode. To log in to the device in FIPS mode through SSH, first log in to the device through a console port, and then create a key pair for the SSH server. • The password for entering the device in FIPS mode must comply with the password control policies, such as password length, complexity, and aging policy. When the aging timer for a password expires, the system prompts you to change the password. If you adjust the system time after the device enters FIPS mode, the login password might expire before the next login because the original system time is generally much earlier than the actual time. If you choose the automatic reboot method, set the system time before executing the fips mode enable command. If you choose the manual reboot method, set the system time before configuring the local username and password. • To use the manual reboot method to enter FIPS mode, you must delete the startup configuration file in binary format after you save the current configuration and specify it as the startup configuration file, and then reboot the device. Otherwise, the commands that are not supported by FIPS mode, if they are in the configuration file, are restored. • The system enters an intermediate state between when the fips mode enable command is executed and when the system is rebooted. If you choose the manual reboot method, do not execute any commands except for the reboot, save, and other commands for entering FIPS mode in the intermediate state. • To switch to non-FIPS mode, execute the undo fips mode enable command in system view, save the configuration, and reboot the device. • Configuration rollback is supported in FIPS mode and it is also supported between FIPS mode and non-FIPS mode. After a configuration rollback between FIPS mode and non-FIPS mode, delete the local user, configure a new local user (local user attributes including password, user role, and service type), save the current configuration file, specify it as the startup configuration file, and 191