HP 6125XLG R2306-HP 6125XLG Blade Switch Security Configuration Guide - Page 97
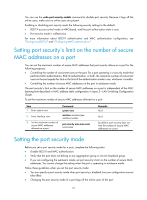
Authentication, Purpose, Security mode, Features that can be, triggered
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 97 highlights
• Authentication-Security modes in this category implement MAC authentication, 802.1X authentication, or a combination of these two authentication methods. Upon receiving a frame, the port in a security mode searches the MAC address table for the source MAC address. If a match is found, the port forwards the frame. If no match is found, the port learns the MAC address or performs authentication, depending on the security mode. If the frame is illegal, the port takes the predefined NTK or intrusion protection action. By default, outgoing frames of a port are not restricted by port security. Only when they trigger the NTK feature, are they restricted by the predefined NTK action. The maximum number of users a port supports equals the maximum number of secure MAC addresses that port security allows or the maximum number of concurrent users the authentication mode in use allows, whichever is smaller. For example, if 802.1X allows more concurrent users than port security's limit on the number of MAC addresses on the port in userLoginSecureExt mode, port security's limit takes effect. Table 4 describes the port security modes and the security features. Table 4 Port security modes Purpose Turning off the port security feature Controlling MAC address learning Performing 802.1X authentication Performing MAC authentication Performing a combination of MAC authentication and 802.1X authentication Security mode noRestriction (the default mode) In this mode, port security is disabled on the port and access to the port is not restricted. autoLearn secure userLogin userLoginSecure userLoginSecureExt userLoginWithOUI macAddressWithRadius macAddressOrUserLoginSecure Or macAddressOrUserLoginSecureExt macAddressElseUserLoginSecure Else macAddressElseUserLoginSecureExt Features that can be triggered N/A NTK/intrusion protection N/A NTK/intrusion protection NTK/intrusion protection NTK/intrusion protection TIP: • userLogin specifies 802.1X authentication and port-based access control. userLogin with Secure specifies 802.1X authentication and MAC-based access control. Ext indicates allowing multiple 802.1X users to be authenticated and serviced at the same time. A security mode without Ext allows only one user to pass 802.1X authentication. • macAddress specifies MAC authentication. • Else specifies that the authentication method before Else is applied first. If the authentication fails, whether to turn to the authentication method following Else depends on the protocol type of the authentication request. • Typically, in a security mode with Or, the authentication method to be used depends on the protocol type of the authentication request. 88