HP 6125XLG R2306-HP 6125XLG Blade Switch Security Configuration Guide - Page 174
Displaying and maintaining IP source guard, Static IPv4 source guard configuration example, Network
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 174 highlights
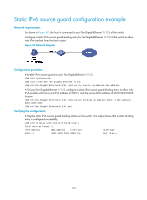
Step 3. Configure a static IPv6 binding entry. Command ipv6 source binding ip-address ipv6-address [ mac-address mac-address ] [ vlan vlan-id ] Remarks By default, no static IPv6 binding entry is configured on an interface. IP source guard does not use the VLAN information (if specified) in static IPv6 source guard binding entries to filter packets. You do not need to specify the VLAN information for packet filtering. The vlan vlan-id option is supported in only Ethernet interface view. NOTE: You cannot configure the same static binding entry on one interface multiple times, but you can configure the same static binding entry on different interfaces. Displaying and maintaining IP source guard Execute display commands in any view and reset commands in user view. For IPv4 source guard: Task Display IPv4 binding entries. Clear IPv4 biding entries. Command display ip source binding [ static | [ vpn-instance vpn-instance-name ] [ dhcp-relay | dhcp-server | dhcp-snooping ] ] [ ip-address ip-address ] [ mac-address mac-address ] [ vlan vlan-id ] [ interface interface-type interface-number ] [ slot slot-number ] reset ip source binding [ static [ ip-address ip-address ] | [ vpn-instance vpn-instance-name ] [ { dhcp-relay | dhcp-server | dhcp-snooping } [ ip-address ip-address ] ] ] For IPv6 source guard: Task Display static IPv6 binding entries. Clear IPv6 biding entries. Command display ipv6 source binding static [ ip-address ipv6-address ] [ mac-address mac-address ] [ vlan vlan-id ] [ interface interface-type interface-number ] [ slot slot-number ] reset ipv6 source binding [ static [ ip-address ipv6-address ] ] Static IPv4 source guard configuration example Network requirements All hosts use static IP addresses. Configure static IPv4 source guard binding entries on Switch A and Switch B to meet the following requirements: • On port Ten-GigabitEthernet 1/1/6 of Switch A, only IP packets from Host C can pass. 165