HP 6125XLG R2306-HP 6125XLG Blade Switch Security Configuration Guide - Page 214
Optional. Enable the Perfect, Forward Secrecy PFS feature
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 214 highlights
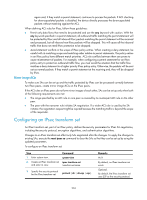
Step 4. Specify the security algorithms. Command • Specify the encryption algorithm for ESP in non-FIPS mode: esp encryption-algorithm { 3des-cbc | aes-cbc-128 | aes-cbc-192 | aes-cbc-256 | des-cbc | null } * • Specify the encryption algorithm for ESP in FIPS mode: esp encryption-algorithm { aes-cbc-128 | aes-cbc-192 | aes-cbc-256 } * • Specify the authentication algorithm for ESP in non-FIPS mode: esp authentication-algorithm { md5 | sha1 } * • Specify the authentication algorithm for ESP in FIPS mode: esp authentication-algorithm sha1 • Specify the authentication algorithm for AH in non-FIPS mode: ah authentication-algorithm { md5 | sha1 } * • Specify the authentication algorithm for AH in FIPS mode: ah authentication-algorithm sha1 Remarks Configure at least one command. By default, no security algorithm is specified. You can specify security algorithms for a security protocol only when the security protocol is used by the transform set. For example, you can specify the ESP-specific security algorithms only when you select ESP or AH-ESP as the security protocol. For ESP, you must specify both the authentication and encryption algorithms. You can specify multiple algorithms by using one command, and the algorithm specified earlier has a higher priority. 5. Specify the mode in which the security protocol encapsulates encapsulation-mode { transport | IP packets. tunnel } By default, the security protocol encapsulates IP packets in tunnel mode. The transport mode applies only when the source and destination IP addresses of data flows match those of the IPsec tunnel. IPsec for IPv6 routing protocols supports only the transport mode. By default, the PFS feature is not used for SA negotiation. For more information about PFS, • In non-FIPS mode: see "Configuring IKE." 6. (Optional.) Enable the Perfect Forward Secrecy (PFS) feature for the IPsec policy. pfs { dh-group1 | dh-group2 | dh-group5 | dh-group14 | dh-group24 } The security level of local Diffie-Hellman group must be higher than or equal that of the • In FIPS mode: peer. pfs dh-group14 The end without the PFS feature performs SA negotiation according to the PFS requirements of the peer end. 205