HP 6125XLG R2306-HP 6125XLG Blade Switch Security Configuration Guide - Page 223
Enabling logging of IPsec packets, Configuring the DF bit of IPsec packets, Command, Remarks, clear
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 223 highlights
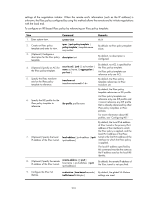
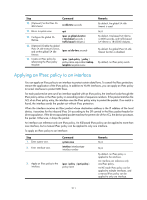
Step 2. Enter IPsec policy view or IPsec policy template view. 3. Enable QoS pre-classify. Command • To enter IPsec policy view: ipsec { policy | ipv6-policy } policy-name seq-number [ isakmp | manual ] • To enter IPsec policy template view: ipsec { policy-template | ipv6-policy-template } template-name seq-number qos pre-classify Remarks Use either command. By default, QoS pre-classify is disabled. Enabling logging of IPsec packets Perform this task to enable the logging of IPsec packets that are discarded because of reasons such as IPsec SA lookup failure, AH-ESP authentication failure, and ESP encryption failure. The log information includes the source and destination IP addresses, the SPI value, and the sequence number of a discarded IPsec packet, and the reason for the failure. To enable the logging of IPsec packets: Step 1. Enter system view. 2. Enable the logging of IPsec packets. Command system-view ipsec invalid-spi-recovery enable Remarks N/A By default, the logging of IPsec packets is disabled. Configuring the DF bit of IPsec packets Perform this task to configure the Don't Fragment (DF) bit in the new IP header of IPsec packets in one of the following ways: • clear-Clears the DF bit in the new header. • set-Sets the DF bit in the new header. • copy-Copies the DF bit in the original IP header to the new IP header. You can configure the DF bit in system view and interface view. The interface-view DF bit setting takes precedence over the system-view DF bit setting. If the interface-view DF bit setting is not configured, the interface uses the system-view DF bit setting. Follow these guidelines when you configure the DF bit: • The DF bit setting takes effect only in tunnel mode, and it changes the DF bit in the new IP header rather than the original IP header. • Configure the same DF bit setting on the interfaces where the same IPsec policy bound to a source interface has been applied. To configure the DF bit of IPsec packets on an interface: 214