HP 6125XLG R2306-HP 6125XLG Blade Switch Security Configuration Guide - Page 187
Configuration guidelines, Configuration procedure, Configuring ARP packet validity check
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 187 highlights
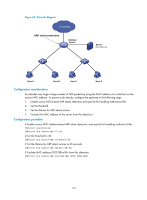
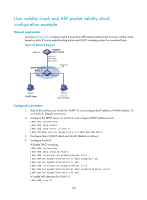
Static IP source guard binding entries are created by using the ip source binding command. For more information, see "Configuring IP source guard." DHCP snooping entries are automatically generated by DHCP snooping. For more information, see Layer 3-IP Services Configuration Guide. Configuration guidelines • Make sure at least one among static IP source guard binding entries and DHCP snooping entries is available for user validity check. Otherwise, ARP packets received from ARP untrusted ports are discarded. • You must specify a VLAN for an IP source guard binding entry. Otherwise, no ARP packets can match the IP source guard binding entry. Configuration procedure To configure user validity check: Step 1. Enter system view. 2. Enter VLAN view. 3. Enable ARP detection. 4. Return to system view. 5. Enter Ethernet interface view or aggregate interface view. 6. (Optional.) Configure the interface as a trusted interface excluded from ARP detection. Command system-view vlan vlan-id arp detection enable quit interface interface-type interface-number arp detection trust Remarks N/A N/A By default, ARP detection is disabled. N/A N/A By default, an interface is untrusted. Configuring ARP packet validity check Enable validity check for ARP packets received on untrusted ports and specify the following objects to be checked: • src-mac-Checks whether the sender MAC address in the message body is identical to the source MAC address in the Ethernet header. If they are identical, the packet is forwarded. Otherwise, the packet is discarded. • dst-mac-Checks the target MAC address of ARP replies. If the target MAC address is all-zero, all-one, or inconsistent with the destination MAC address in the Ethernet header, the packet is considered invalid and discarded. • ip-Checks the sender and target IP addresses of ARP replies, and the sender IP address of ARP requests. All-zero, all-one, or multicast IP addresses are considered invalid and the corresponding packets are discarded. To configure ARP packet validity check: Step 1. Enter system view. 2. Enter VLAN view. Command system-view vlan vlan-id Remarks N/A N/A 178