HP 6125XLG R2306-HP 6125XLG Blade Switch Security Configuration Guide - Page 216
Configuring an IKE-based IPsec policy
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 216 highlights
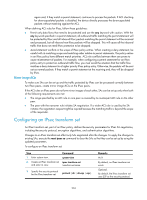
Step 6. Specify the remote IP address of the IPsec tunnel. 7. Configure an SPI for the inbound or outbound IPsec SA. 8. Configure keys for the IPsec SA. Command Remarks By default, the remote IP address of the IPsec tunnel is not specified. remote-address { ipv4-address | ipv6 ipv6-address } The local IPv4 address of the IPsec tunnel is the primary IP address of the interface to which the IPsec policy is applied. The local IPv6 address of the IPsec tunnel is the first IPv6 address of the interface to which the IPsec policy is applied. • To configure an SPI for the inbound IPsec SA: sa spi inbound { ah | esp } spi-number • To configure an SPI for the outbound IPsec SA: sa spi outbound { ah | esp } spi-number By default, no SPI is configured for the inbound or outbound IPsec SA. • Configure an authentication key in hexadecimal format for AH: sa hex-key authentication { inbound | outbound } ah { cipher | simple } key-value • Configure an authentication By default, no keys are configured for the key in character format for AH: IPsec SA. sa string-key { inbound | outbound } ah { cipher | simple } key-value • Configure a key in character format for ESP: Configure keys correctly for the security protocol (AH, ESP, or both) you have specified in the IPsec transform set referenced by the IPsec policy. sa string-key { inbound | If you configure a key in both the outbound } esp { cipher | character and hexadecimal formats, only simple } key-value the most recent configuration takes • Configure an authentication effect. key in hexadecimal format for If you configure a key in character format ESP: for ESP, the device automatically sa hex-key authentication generates an authentication key and an { inbound | outbound } esp encryption key for ESP. { cipher | simple } key-value • Configure an encryption key in hexadecimal format for ESP: sa hex-key encryption { inbound | outbound } esp { cipher | simple } key-value Configuring an IKE-based IPsec policy In an IKE-based IPsec policy, the parameters are automatically negotiated through IKE. To configure an IKE-based IPsec policy, use one of the following methods: • Directly configure it by configuring the parameters in IPsec policy view. 207