HP GbE2c HP GbE2c Ethernet Blade Switch for c-Class BladeSystem Application Gu - Page 20
RADIUS authentication features - default password
 |
UPC - 808736802215
View all HP GbE2c manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 20 highlights
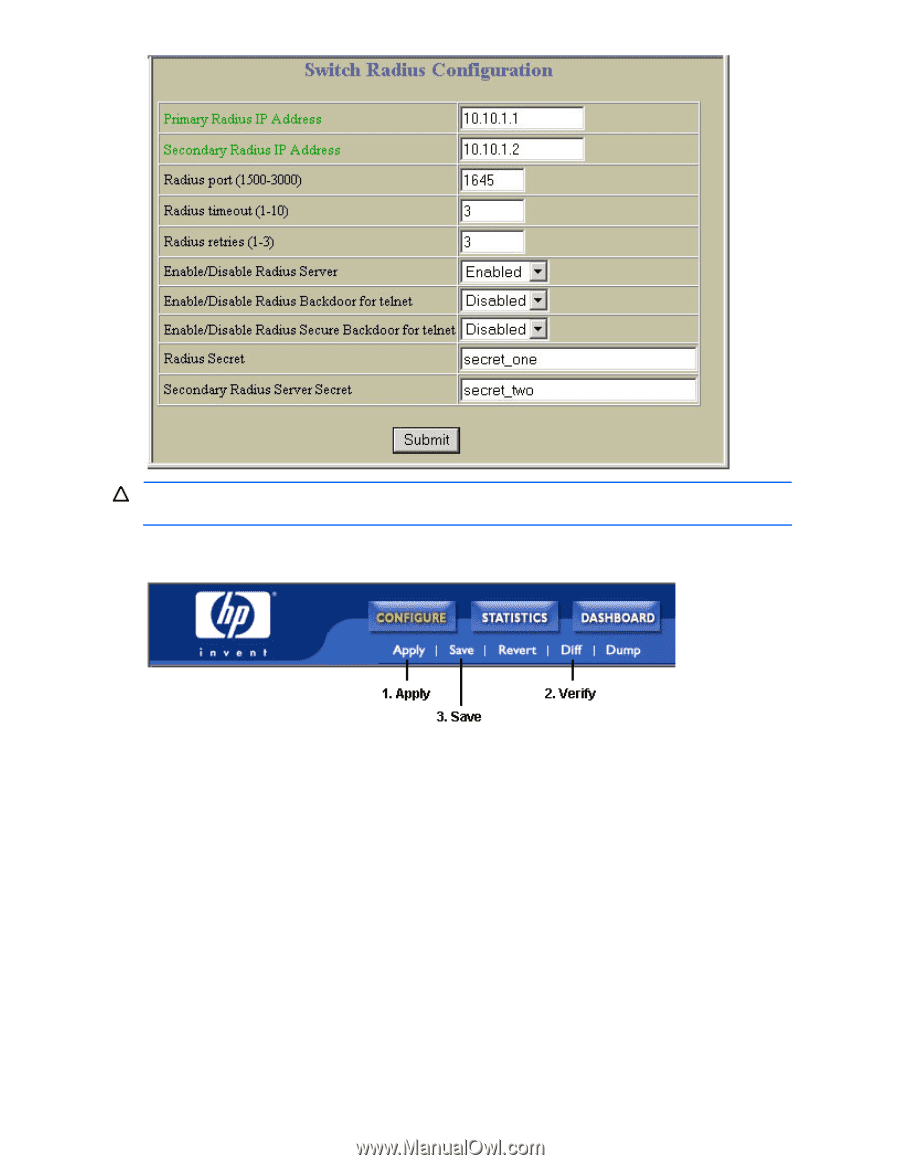
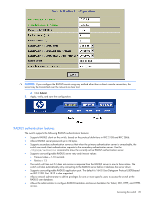
CAUTION: If you configure the RADIUS secret using any method other than a direct console connection, the secret may be transmitted over the network as clear text. d. Click Submit. 2. Apply, verify, and save the configuration. RADIUS authentication features The switch supports the following RADIUS authentication features: • Supports RADIUS client on the switch, based on the protocol definitions in RFC 2138 and RFC 2866. • Allows RADIUS secret password up to 32 bytes. • Supports secondary authentication server so that when the primary authentication server is unreachable, the switch can send client authentication requests to the secondary authentication server. Use the /cfg/sys/radius/cur command to show the currently active RADIUS authentication server. • Supports user-configurable RADIUS server retry and time-out values: • Time-out value = 1-10 seconds • Retries = 1-3 • The switch will time out if it does not receive a response from the RADIUS server in one to three retries. The switch will also automatically retry connecting to the RADIUS server before it declares the server down. • Supports user-configurable RADIUS application port. The default is 1645/User Datagram Protocol (UDP)-based on RFC 2138. Port 1812 is also supported. • Allows network administrator to define privileges for one or more specific users to access the switch at the RADIUS user database. • Allows the administrator to configure RADIUS backdoor and secure backdoor for Telnet, SSH, HTTP, and HTTPS access. Accessing the switch 20