HP GbE2c HP GbE2c Ethernet Blade Switch for c-Class BladeSystem Application Gu - Page 76
Con Access Control Lists and Groups (BBI example 1), Con Access Control Lists ACLs.
 |
UPC - 808736802215
View all HP GbE2c manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 76 highlights
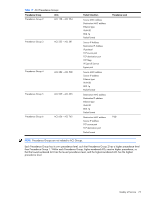
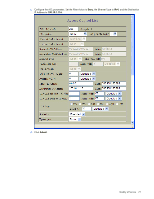
In this example, all traffic that ingresses on port 20 with source IP from the class 100.10.1.0/24 and destination IP 200.20.1.116 is denied. Example 3: Use this configuration to block traffic from a source that is destined for a specific egress port. >> Main# /cfg/acl/acl 1 (Define ACL 1) >> ACL 1# ethernet/smac 002100000000 ffffffffffff >> Filtering Ethernet# .. >> ACL 1# action deny >> ACL 1# stats e >> ACL 1# /cfg/acl/acl 255 (Define ACL 255) >> ACL 255# egrport 24 >> ACL 255# action deny >> ACL 255# stats e >> ACL 255# /cfg/port 23/aclqos >> Port 23 ACL# add acl 1 (Add ACL 1 to port 23) >> Port 23 ACL# add acl 255 (Add ACL 255 to port 23) >> Port 23 ACL# apply >> Port 23 ACL# save In this example, all traffic (Layer 2 known unicast) that ingresses on port 23 from source MAC 00:21:00:00:00:00 and is destined for port 24 is denied. Configure Access Control Lists and Groups (BBI example 1) 1. Configure Access Control Lists (ACLs). a. Click the Configure context button on the Toolbar. b. Open the Access Control Lists folder, and select Add ACL. Quality of Service 76