HP GbE2c HP GbE2c Ethernet Blade Switch for c-Class BladeSystem Application Gu - Page 71
Using ACL filters, Summary of packet classifiers - vlan vrrp
 |
UPC - 808736802215
View all HP GbE2c manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 71 highlights
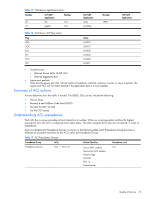
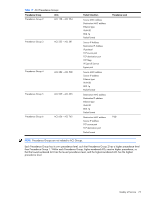
• Queue and schedule traffic: • Place packets in one of two COS queues • Schedule transmission based on the COS queue weight Using ACL filters Access Control Lists are filters that allow you to classify and segment traffic, so you can provide different levels of service to different traffic types. Each filter defines the conditions that must match for inclusion in the filter, and also the actions that are performed when a match is made. Summary of packet classifiers The GbE2c allows you to classify packets based on various parameters, such as: • Ethernet • Source MAC address/mask • Destination MAC address/mask • VLAN number/mask • Ethernet type • Ethernet Priority, which is the IEEE 802.1p Priority • IPv4 • Source IP address/mask • Destination IP address/mask • Type of Service value • IP protocol number: The protocol number or name as shown in the following table: Table 14 Well-known protocol types Number Protocol Name 1 icmp 2 igmp 6 tcp 17 udp 89 ospf 112 vrrp • TCP/UDP • TCP/UDP application source port, as shown in the table titled "Well-Known Application Ports" • TCP/UDP application destination port, as shown in the table titled "Well-Known Application Ports" • TCP/UDP flag value, as shown in the table titled "Well-Known TCP Flag Values" Table 15 Well-known application ports Number TCP/UDP Application Number TCP/UDP Application Number TCP/UDP Application 20 ftp-data 79 finger 179 irc 21 ftp 80 http 194 imap3 22 ssh 109 pop2 220 ldap 23 telnet 110 pop3 389 https 25 smtp 111 sunrpc 443 rip 37 time 119 nntp 520 rtsp 42 name 123 ntp 554 Radius 43 whois 143 imap 1645;1812 Radius Accounting 53 domain 144 news 1813 hsrp Quality of Service 71