HP GbE2c HP GbE2c Ethernet Blade Switch for c-Class BladeSystem Application Gu - Page 75
Re-marking, Viewing ACL statistics, ACL configuration examples - reset
 |
UPC - 808736802215
View all HP GbE2c manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 75 highlights
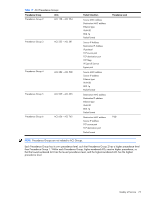
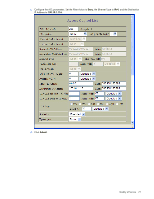
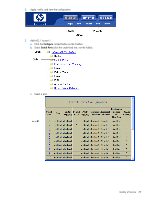
Using meters, you set a Committed Rate in Kb/s (1024 bits per second in each Kb/s). All traffic within this Committed Rate is In-Profile. Additionally, you set a Maximum Burst Size that specifies an allowed data burst larger than the Committed Rate for a brief period. These parameters define the In-Profile traffic. Meters keep the sorted packets within certain parameters. You can configure a meter on an ACL, and perform actions on metered traffic, such as packet re-marking. Re-marking Re-marking allows for the treatment of packets to be reset based on new network specifications or desired levels of service. You can configure the ACL to re-mark a packet as follows: • Change the DSCP value of a packet, used to specify the service level traffic should receive. • Change the 802.1p priority of a packet. Viewing ACL statistics ACL statistics display how many packets hit (matched) each ACL. Up to 64 statistic counters can be displayed for each ACL Precedence Group. Use ACL statistics to check filter performance, and debug the ACL filters. You must enable statistics (cfg/acl/acl x/stats ena) for each ACL that you want to monitor. ACL configuration examples Configure Access Control Lists (CLI example) The following configuration examples illustrate how to use Access Control Lists (ACLs) to block traffic. These basic configurations illustrate common principles of ACL filtering. NOTE: Each ACL filters traffic that ingresses on the port to which the ACL is added. The egrport classifier filters traffic that ingresses the port to which the ACL is added, and then egresses the port specified by egrport. In most common configurations, egrport is not used. Example 1: Use this configuration to block traffic to a specific host. >> Main# /cfg/acl/acl 255 >> ACL 255# ipv4/dip 100.10.1.116 255.255.255.255 >> Filtering IPv4# .. >> ACL 255# action deny >> ACL 255# /cfg/port 20/aclqos >> Port 20 ACL# add acl 255 >> Port 20 ACL# apply >> Port 20 ACL# save (Define ACL 255) (Add ACL to port 20) In this example, all traffic that ingresses on port 20 is denied if it is destined for the host at IP address 100.10.1.116. Example 2: Use this configuration to block traffic from a network destined for a specific host address. >> Main# /cfg/acl/acl 256 >> ACL 256# ipv4/sip 100.10.1.0 255.255.255.0 >> ACL 256# ipv4/dip 200.20.1.116 255.255.255.255 >> Filtering IPv4# .. >> ACL 256# action deny >> ACL 256# /cfg/port 20/aclqos >> Port 20 ACL# add acl 256 >> Port 20 ACL# apply >> Port 20 ACL# save (Define ACL 256) (Add ACL to port 20) Quality of Service 75