HP GbE2c HP GbE2c Ethernet Blade Switch for c-Class BladeSystem Application Gu - Page 40
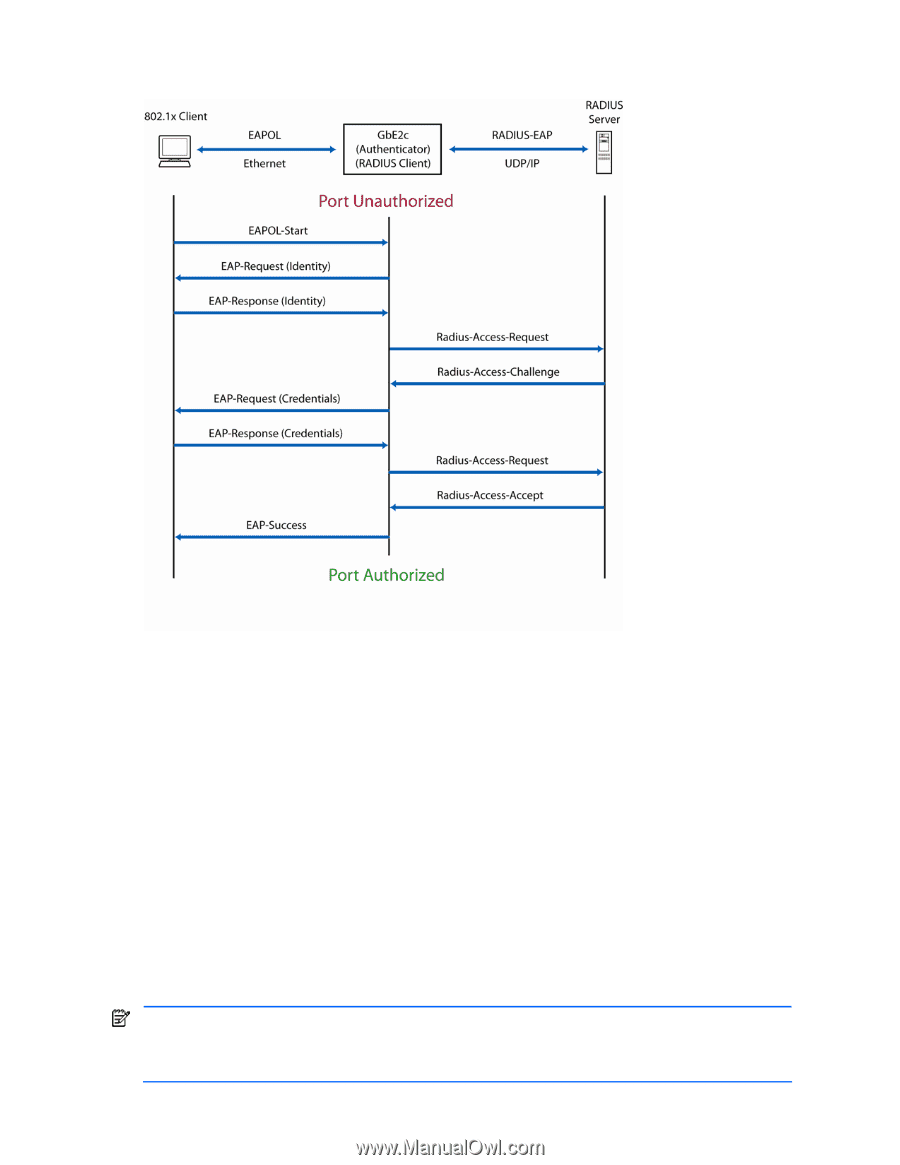
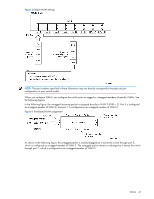
EAPoL Message Exchange
 |
UPC - 808736802215
View all HP GbE2c manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 40 highlights
The following figure shows a typical message exchange initiated by the client. Figure 2 Using EAPoL to authenticate a port EAPoL Message Exchange During authentication, EAPOL messages are exchanged between the client and the switch authenticator, while RADIUS-EAP messages are exchanged between the switch authenticator and the Radius authentication server. Authentication is initiated by one of the following methods: Switch authenticator sends an EAP-Request/Identity packet to the client. Client sends an EAPOL-Start frame to the switch authenticator, which responds with an EAP-Request/Identity frame. The client confirms its identity by sending an EAP-Response/Identity frame to the switch authenticator, which forwards the frame encapsulated in a RADIUS packet to the server. The Radius server chooses an EAP-supported authentication algorithm to verify the client's identity, and sends an EAPRequest packet to the client via the switch authenticator. The client then replies to the Radius server with an EAPResponse containing its credentials. Upon a successful authentication of the client by the server, the 802.1x-controlled port transitions from unauthorized to authorized state, and the client is allowed full access to services through the controlled port. When the client later sends an EAPOL-Logoff message to the switch authenticator, the port transitions from authorized to unauthorized state. If a client that does not support 802.1x connects to an 802.1x-controlled port, the switch authenticator requests the client's identity when it detects a change in the operational state of the port. The client does not respond to the request, and the port remains in the unauthorized state. NOTE: When an 802.1x-enabled client connects to a port that is not 802.1x-controlled, the client initiates the authentication process by sending an EAPOL-Start frame. When no response is received, the client retransmits the request for a fixed number of times. If no response is received, the client assumes the port is in authorized state, and begins sending frames, even if the port is unauthorized. Port-based Network Access and traffic control 40