D-Link DSR-150N DSR-150 User Manual - Page 117
Configuring IPsec Policies
 |
View all D-Link DSR-150N manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 117 highlights
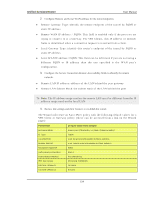
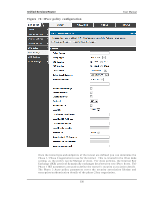
Unified Services Router Par am eter Exchange Mode ID Type Local WAN ID Remote WAN ID Encryption Algorithm Authentication Algorithm Authentication Method PFS Key-Group Life Time (Phase 1) NETBIOS De f au lt value f rom Wizard Aggressive (Client policy ) or Main (Gatew ay policy) FQDN w an_local.com(only applies to Client policies) w an_remote.com(only applies to Client policies) 3DES SHA-1 Pre-shared Key DH-Group 2(1024 bit) 24 hours Enabled (only applies to Gatew ay policies) User Manual Th e VPN W izard is t h e reco mmen d ed met h o d t o s et u p an A u t o IPs ec p o licy . On ce t h e W izard creat es t h e mat ch in g IKE an d VPN p o licies req u ired b y t h e A u t o p o licy , o n e can mo d ify t h e req uired field s t h ro ugh t he ed it lin k. Refer t o t h e o n lin e help for details . Eas y Set u p Sit e t o Sit e VPN Tu n n el: If y o u fin d it d ifficu lt t o co n fig u re VPN p o licies t h ro ugh VPN wizard u s e easy s et up s it e t o s it e VPN t u n n el. Th is will ad d VPN p o licies b y imp o rt in g a file co n t ain in g v pn policies . 6.2 Configuring IPsec Policies Setup > VPN Settings > IPsec > IPsec Policies A n IPs ec policy is between this router and another gateway or this router and a IPs ec clien t o n a remo t e h o s t . Th e IPs ec mo d e can b e eit her t u nnel o r t ran s p o rt d ep en d in g on the network being travers ed between the two policy endpoints . Tran s p ort : Th is is u sed fo r en d -to -en d co mmu n icat ion b et ween t h is ro u t er an d t h e t u n n el en d p o in t , eit h er an o t h er IPs ec g at eway o r an IPs ec VPN clien t o n a h o s t . On ly t h e d at a p ay lo ad is en cry pted an d t he IP h ead er is n o t mo d ified o r en cry p t ed . Tu n n el: Th is mo d e is u s ed fo r n et wo rk -t o -n et wo rk IPs ec t u n n els wh ere t h is g at eway is o n e en dpo int o f t h e t u nn el. In t h is mo d e t h e en t ire IP p acket in clu d in g the header is encrypted and/or authenticated. W h en t u n n el mo d e is s elect ed , y o u can en ab le Net BIOS an d DHCP o v er IPs ec . DHCP o v er IPs ec allo ws t h is ro ut er t o s erve IP leas es t o h o sts o n t h e remo t e LA N. A s well in t h is mo d e y o u can d efin e t h e s ing le IP ad d ress, ran ge o f IPs , o r s u b net o n b oth t h e lo cal an d remo t e p riv at e n et wo rks t h at can co mmu n icat e o v er t h e t u n n el. 115