Netgear FVS338 FVS338 Reference Manual - Page 184
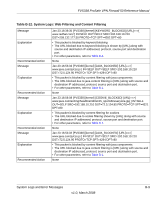
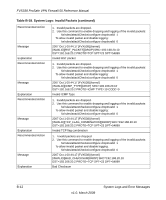
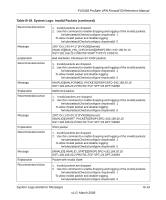
Table B-18. System Logs: Invalid Packets continued
 |
UPC - 606449037197
View all Netgear FVS338 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 184 highlights
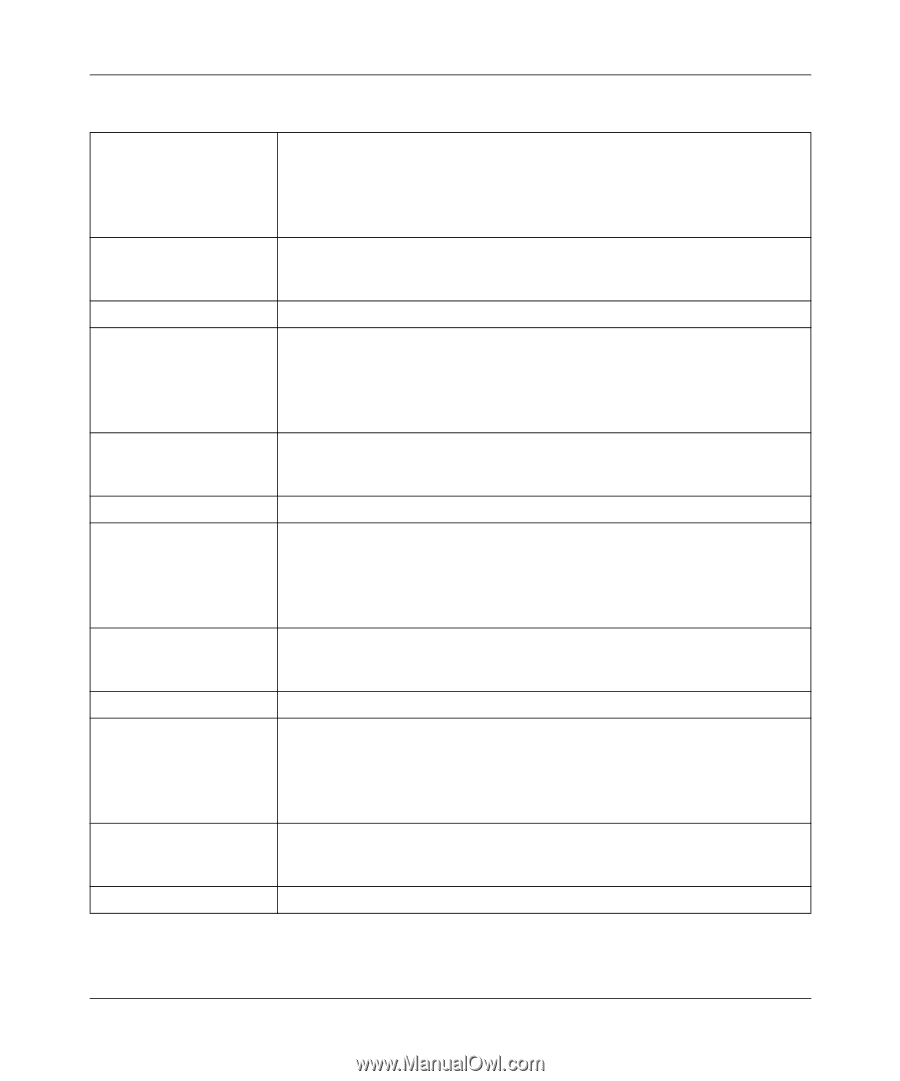
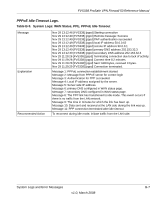
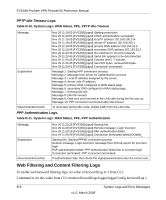
FVS338 ProSafe VPN Firewall 50 Reference Manual Table B-18. System Logs: Invalid Packets (continued) Recommended Action Message Explanation Recommended Action Message Explanation Recommended Action Message Explanation Recommended Action Message Explanation 1. Invalid packets are dropped. 2. Use this command to enable dropping and logging of the invalid packets: fw/rules/attackChecks/configure dropInvalid 1 To allow invalid packet and disable logging: fw/rules/attackChecks/configure dropInvalid 0 2007 Oct 1 00:44:17 [FVX538] [kernel] [INVALID][RST_PACKET][DROP] SRC=192.168.20.10 DST=192.168.20.2 PROTO=TCP SPT=23 DPT=54899 Invalid RST packet 1. Invalid packets are dropped. 2. Use this command to enable dropping and logging of the invalid packets: fw/rules/attackChecks/configure dropInvalid 1 To allow invalid packet and disable logging: fw/rules/attackChecks/configure dropInvalid 0 2007 Oct 1 00:44:17 [FVX538] [kernel] [INVALID][ICMP_TYPE][DROP] SRC=192.168.20.10 DST=192.168.20.2 PROTO=ICMP TYPE=19 CODE=0 Invalid ICMP Type 1. Invalid packets are dropped. 2. Use this command to enable dropping and logging of the invalid packets: fw/rules/attackChecks/configure dropInvalid 1 To allow invalid packet and disable logging: fw/rules/attackChecks/configure dropInvalid 0 2007 Oct 1 00:44:17 [FVX538] [kernel] [INVALID][TCP_FLAG_COMBINATION][DROP] SRC=192.168.20.10 DST=192.168.20.2 PROTO=TCP SPT=23 DPT=54899 Invalid TCP flag combination 1. Invalid packets are dropped. 2. Use this command to enable dropping and logging of the invalid packets: fw/rules/attackChecks/configure dropInvalid 1 To allow invalid packet and disable logging: fw/rules/attackChecks/configure dropInvalid 0 2007 Oct 1 00:44:17 [FVX538] [kernel] [INVALID][BAD_CHECKSUM]DROP] SRC=192.168.20.10 DST=192.168.20.2 PROTO=TCP SPT=23 DPT=54899 Bad Checksum B-12 v1.0, March 2008 System Logs and Error Messages