Netgear FVS338 FVS338 Reference Manual - Page 84
Setting Up Port Triggering, Delete, Apply, Security, Port Triggering, Triggering
 |
UPC - 606449037197
View all Netgear FVS338 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 84 highlights
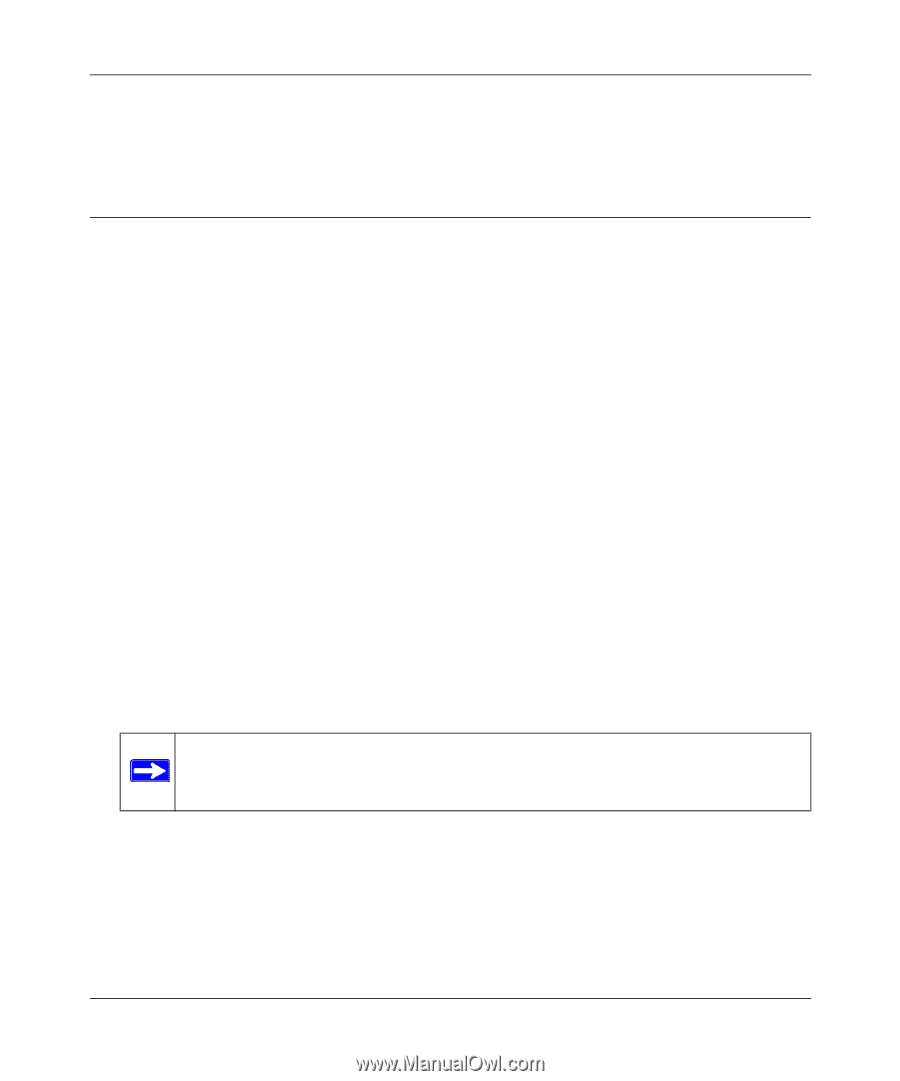
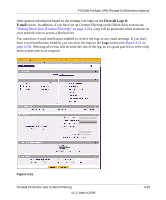
FVS338 ProSafe VPN Firewall 50 Reference Manual 4. To remove an entry from the table, select the IP/MAC Bind entry and click Delete. 5. Click Apply to save your settings. Setting Up Port Triggering Port triggering allows some applications running on a LAN network to be available to external applications that would otherwise be partially blocked by the firewall. Using this feature requires that you know the port numbers used by the Application. Once configured, Port Triggering operates as follows: 1. A PC makes an outgoing connection using a port number defined in the Port Triggering table. 2. The VPN firewall records this connection, opens the an INCOMING port or ports associated with this entry in the Port Triggering table, and associates them with the PC. 3. The remote system receives the PCs request and responds using the different port numbers that you have now opened. 4. The VPN firewall matches the response to the previous request, and forwards the response to the PC. Without Port Triggering, this response would be treated as a new connection request rather than a response. As such, it would be handled in accordance with the Port Forwarding rules: • Only one PC can use a Port Triggering application at any time. • After a PC has finished using a Port Triggering application, there is a Time-out period before the application can be used by another PC. This is required because this Router cannot be sure when the application has terminated. Note: For additional ways of allowing inbound traffic, see "LAN WAN Inbound Services Rules" on page 4-9. To add a Port triggering rule: 1. Select Security from the main menu and Port Triggering from the submenu. The Port Triggering screen will display. 1. Enter a user-defined name for this rule in the Name field. 4-28 Firewall Protection and Content Filtering v1.0, March 2008