Netgear FVS338 FVS338 Reference Manual - Page 92
Administrator Information
 |
UPC - 606449037197
View all Netgear FVS338 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 92 highlights
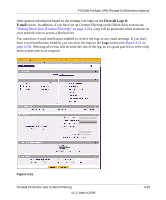
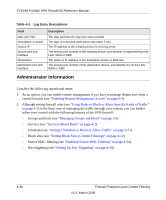
FVS338 ProSafe VPN Firewall 50 Reference Manual Table 4-3. Log Entry Descriptions Field Date and Time Description or Action Source IP Source port and interface Destination Destination port and interface Description The date and time the log entry was recorded. The type of event and what action was taken if any. The IP address of the initiating device for this log entry. The service port number of the initiating device, and whether it originated from the LAN, WAN or DMZ. The name or IP address of the destination device or Web site. The service port number of the destination device, and whether it's on the LAN, WAN or DMZ. Administrator Information Consider the following operational items: 1. As an option, you can enable remote management if you have to manage distant sites from a central location (see "Enabling Remote Management Access" on page 6-9). 2. Although setting firewall rules (see "Using Rules to Block or Allow Specific Kinds of Traffic" on page 4-1) is the basic way of managing the traffic through your system, you can further refine your control with the following features of the VPN firewall: - Groups and hosts (see "Managing Groups and Hosts" on page 3-6) - Services (see "Services-Based Rules" on page 4-2) - Schedules (see "Setting a Schedule to Block or Allow Traffic" on page 4-21) - Block sites (see "Setting Block Sites (Content Filtering)" on page 4-22) - Source MAC filtering (see "Enabling Source MAC Filtering" on page 4-24) - Port triggering (see "Setting Up Port Triggering" on page 4-28) 4-36 Firewall Protection and Content Filtering v1.0, March 2008