Ricoh SP C250DN Operating Instructions - Page 10
Differences in Functions between Different Models, Note to Administrator, Password, User Restriction
 |
View all Ricoh SP C250DN manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 10 highlights
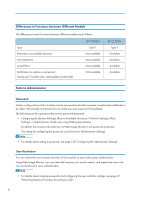
Differences in Functions between Different Models The differences in main functions between different models are as follows: Type Restrictions on available functions User Restriction Locked Print Notification to replace a component (Fusing unit, Transfer roller, Intermediate transfer belt) SP C250DN Type 1 Not available Not available Not available Not available SP C252DN Type 2 Available Available Available Available Note to Administrator Password Certain configurations of this machine can be password-protected to prevent unauthorized modifications by others. We strongly recommend you to create your own password immediately. The following are the operations that can be password-protected: • Configuring the [System Settings], [Restrict Available Functions], [Network Settings], [IPsec Settings], or [Administrator Tools] menu using Web Image Monitor By default, the access to the machine via Web Image Monitor is not password-protected. The setting for configuring the password can be found in [Administrator Settings]. • For details about setting a password, see page 126 "Configuring the Administrator Settings". User Restriction You can restrict the use of certain functions of this machine to users with proper authentication. Using Web Image Monitor, you can select the functions you want to restrict, and register the users who can use that function upon authentication. • For details about creating passwords and configuring the user restriction settings, see page 37 "Restricting Machine Functions According to User". 8