HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 101
Configuration procedure, and password
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 101 highlights
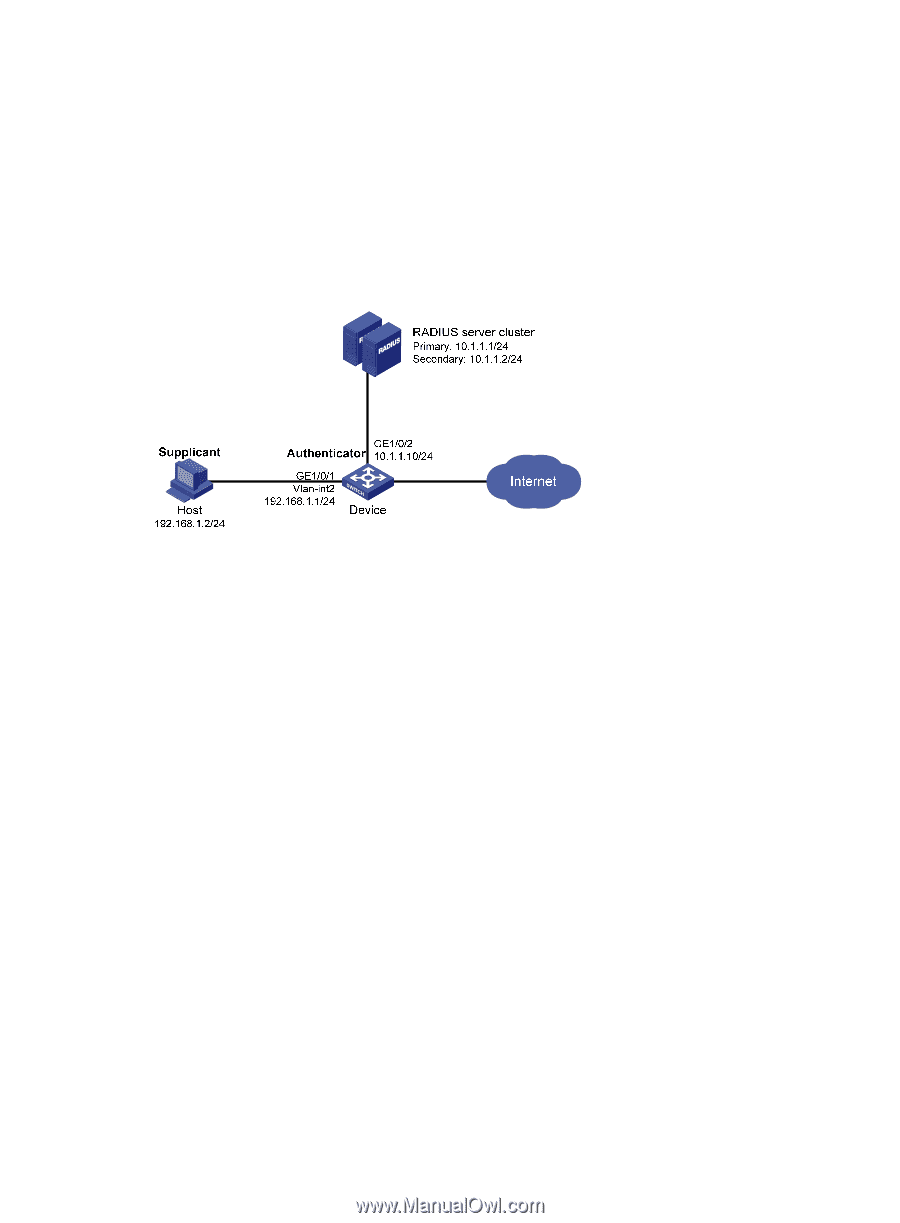
Use RADIUS servers to perform authentication, authorization, and accounting for the 802.1X users. If RADIUS authentication fails, perform local authentication on the access device. If RADIUS accounting fails, the access device logs the user off. Configure the host at 10.1.1.1/24 as the primary authentication and accounting servers, and the host at 10.1.1.2/24 as the secondary authentication and accounting servers. Assign all users to the ISP domain aabbcc.net, which accommodates up to 30 users. Configure the shared key as name for packets between the access device and the authentication server, and the shared key as money for packets between the access device and the accounting server. Figure 33 Network diagram Configuration procedure 1. Configure the 802.1X client. If HP iNode is used, do not select the Carry version info option in the client configuration. (Details not shown.) 2. Configure the RADIUS servers and add user accounts for the 802.1X users. For information about the RADIUS commands used on the access device in this example, see Security Command Reference. (Details not shown.) 3. Assign an IP address to each interface on the access device. (Details not shown.) 4. Configure user accounts for the 802.1X users on the access device: # Add a local user with the username localuser, and password localpass in plaintext. (Make sure the username and password are the same as those configured on the RADIUS server.) system-view [Device] local-user localuser [Device-luser-localuser] service-type lan-access [Device-luser-localuser] password simple localpass # Configure the idle cut function to log off any online user that has been idled for 20 minutes. [Device-luser-localuser] authorization-attribute idle-cut 20 [Device-luser-localuser] quit 5. Configure a RADIUS scheme: # Create the RADIUS scheme radius1 and enter its view. [Device] radius scheme radius1 # Specify the IP addresses of the primary authentication and accounting RADIUS servers. [Device-radius-radius1] primary authentication 10.1.1.1 [Device-radius-radius1] primary accounting 10.1.1.1 91