HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 61
Verifying the configuration, AAA for 802.1X users by a RADIUS server, Network requirements
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 61 highlights
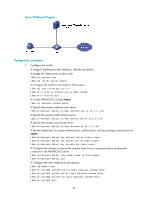
[Switch] radius scheme rad # Specify the primary authentication server. [Switch-radius-rad] primary authentication 10.1.1.1 1812 # Set the shared key for secure authentication communication to expert. [Switch-radius-rad] key authentication expert # Configure the scheme to include the domain names in usernames to be sent to the RADIUS server. [Switch-radius-rad] user-name-format with-domain # Specify the service type for the RADIUS server, which must be extended when the RADIUS server runs on IMC. [Switch-radius-rad] server-type extended [Switch-radius-rad] quit # Configure the AAA methods for the domain. [Switch] domain bbb [Switch-isp-bbb] authentication login radius-scheme rad [Switch-isp-bbb] authorization login radius-scheme rad [Switch-isp-bbb] quit Verifying the configuration After you complete the configuration, the SSH user should be able to use the configured account to access the user interface of the switch and can access the demands of level 0 through level 3. . # Use the display connection command to view the connection information on the switch. [Switch] display connection Index=1 ,Username=hello@bbb IP=192.168.1.58 IPv6=N/A Total 1 connection(s) matched. AAA for 802.1X users by a RADIUS server Network requirements As shown in Figure 15, configure the switch to: • Use the RADIUS server for authentication, authorization, and accounting of 802.1X users. • Use MAC-based access control on GigabitEthernet 1/0/1 to authenticate all 802.1X users on the port separately. • Keep the domain names in usernames sent to the RADIUS server. On the RADIUS server, add a service that charges 120 dollars for up to 120 hours per month and assigns authenticated users to VLAN 4, create an account named dot1x@bbb for 802.1X users, and assign the service to the account. Set the shared keys for secure RADIUS communication to expert. Set the ports for authentication/authorization and accounting to 1812 and 1813, respectively. 51