HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 184
Configuration procedure, Configuring SSL, Con the PKI domain
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 184 highlights
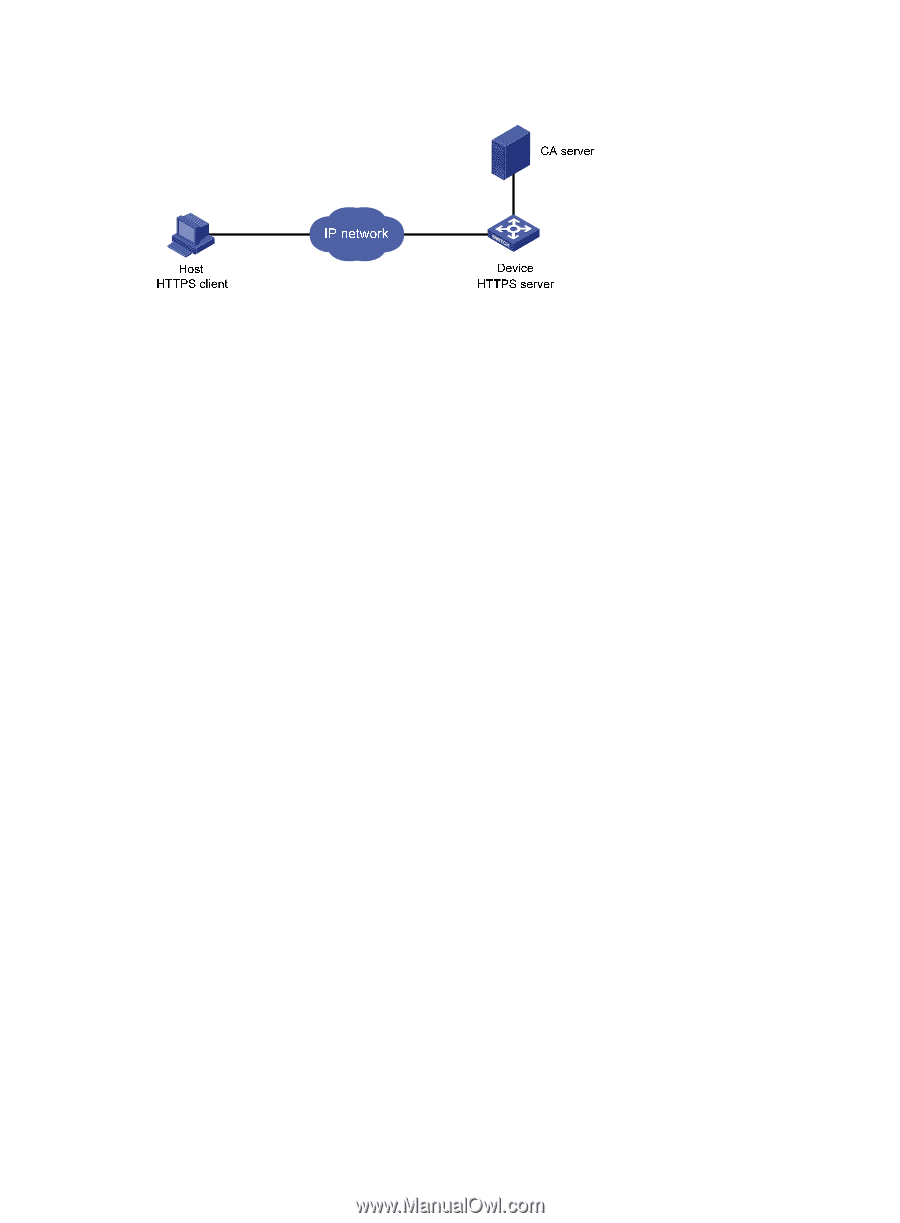
Figure 48 Network diagram Configuration procedure The configuration procedure involves SSL configuration and HTTPS configuration. For more information about SSL configuration, see "Configuring SSL." For more information about HTTPS configuration, see Fundamentals Configuration Guide. The PKI domain to be referenced by the SSL policy must exist. For how to configure a PKI domain, see "Configure the PKI domain:." The configuration procedure is as follows: 1. Configure the HTTPS server: # Configure the SSL policy for the HTTPS server to use. system-view [Device] ssl server-policy myssl [Device-ssl-server-policy-myssl] pki-domain 1 [Device-ssl-server-policy-myssl] client-verify enable [Device-ssl-server-policy-myssl] quit 2. Configure the certificate attribute group: # Create certificate attribute group mygroup1 and add two attribute rules. The first rule defines that the DN of the subject name includes the string aabbcc, and the second rule defines that the IP address of the certificate issuer is 10.0.0.1. [Device] pki certificate attribute-group mygroup1 [Device-pki-cert-attribute-group-mygroup1] attribute 1 subject-name dn ctn aabbcc [Device-pki-cert-attribute-group-mygroup1] attribute 2 issuer-name ip equ 10.0.0.1 [Device-pki-cert-attribute-group-mygroup1] quit # Create certificate attribute group mygroup2 and add two attribute rules. The first rule defines that the FQDN of the alternative subject name does not include the string of apple, and the second rule defines that the DN of the certificate issuer name includes the string aabbcc. [Device] pki certificate attribute-group mygroup2 [Device-pki-cert-attribute-group-mygroup2] attribute 1 alt-subject-name fqdn nctn apple [Device-pki-cert-attribute-group-mygroup2] attribute 2 issuer-name dn ctn aabbcc [Device-pki-cert-attribute-group-mygroup2] quit 3. Create a certificate attribute access control policy named myacp and add two access control rules. [Device] pki certificate access-control-policy myacp [Device-pki-cert-acp-myacp] rule 1 deny mygroup1 [Device-pki-cert-acp-myacp] rule 2 permit mygroup2 [Device-pki-cert-acp-myacp] quit 174