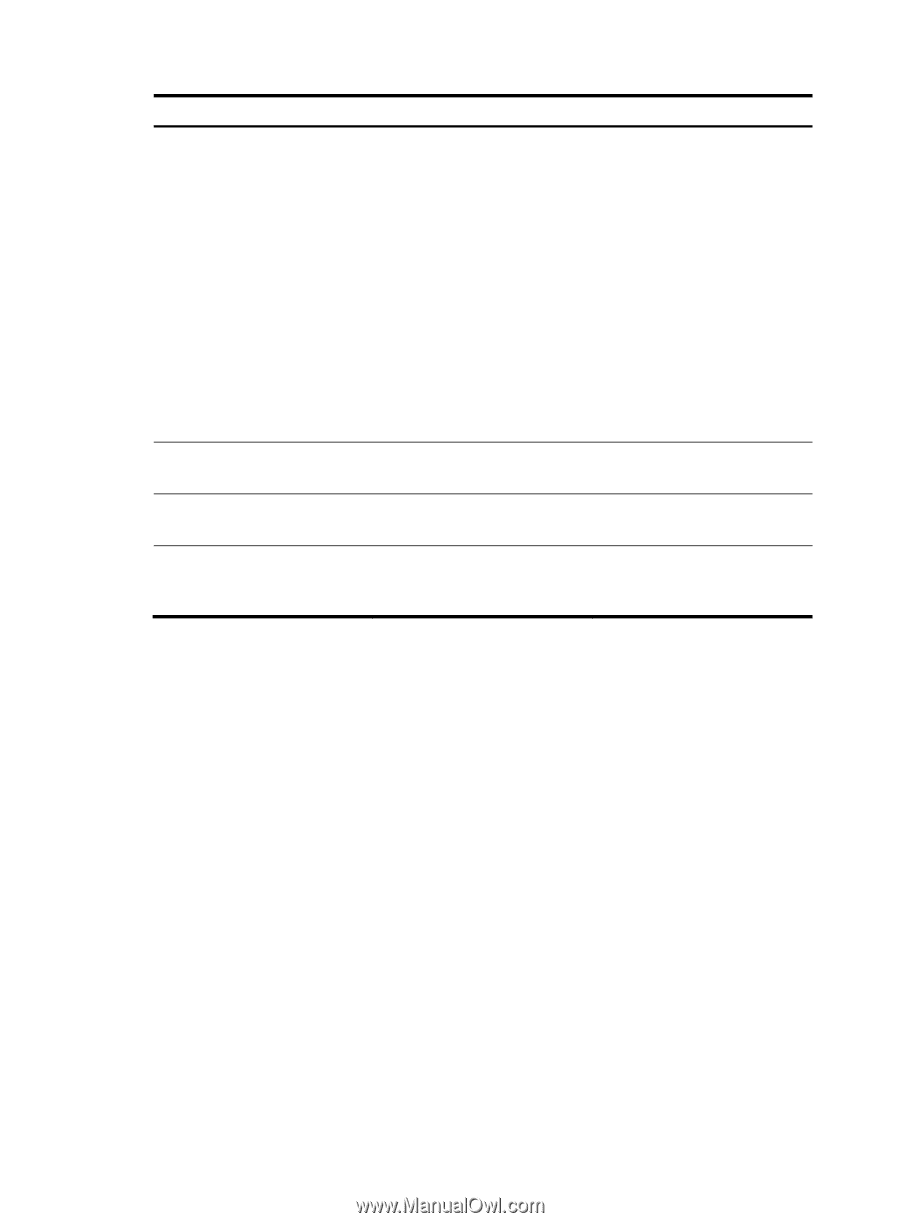HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 28
Configuring user group attributes, user privilege level
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 28 highlights
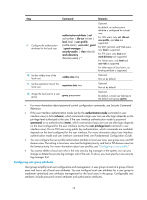
Step Command Remarks 9. Configure the authorization attributes for the local user. authorization-attribute { acl acl-number | dle-cut minute | level level | user-profile profile-name | user-role { guest | guest-manager | security-audit } | vlan vlan-id | work-directory directory-name } * Optional. By default, no authorization attribute is configured for a local user. For LAN users, only acl, idle-cut, user-profile, and vlan are supported. For SSH, terminal, and Web users, only level is supported. For FTP users, only level and work-directory are supported. For Telnet users, only level and user-role is supported. For other types of local users, no binding attribute is supported. 10. Set the validity time of the local user. validity-date time Optional. Not set by default. 11. Set the expiration time of the local user. expiration-date time Optional. Not set by default. 12. Assign the local user to a user group. group group-name Optional. By default, a local user belongs to the default user group system. • For more information about password control configuration commands, see Security Command Reference. • If the user interface authentication mode (set by the authentication-mode command in user interface view) is AAA (scheme), which commands a login user can use after login depends on the privilege level authorized to the user. If the user interface authentication mode is password (password) or no authentication (none), which commands a login user can use after login depends on the level configured for the user interface (set by the user privilege level command in user interface view). For an SSH user using public key authentication, which commands are available depends on the level configured for the user interface. For more information about user interface authentication mode and user interface command level, see Fundamentals Configuration Guide. • You can configure the user profile authorization attribute in local user view, user group view, and ISP domain view. The setting in local user view has the highest priority, and that in ISP domain view has the lowest priority. For more information about user profiles, see "Configuring a user profile." • You cannot delete a local user who is the only security log manager in the system, nor can you change or delete the security log manager role of the user. To do so, you must specify a new security log manager first. Configuring user group attributes User groups simplify local user configuration and management. A user group consists of a group of local users and has a set of local user attributes. You can configure local user attributes for a user group to implement centralized user attributes management for the local users in the group. Configurable user attributes include password control attributes and authorization attributes. 18