HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 240
Verifying the configuration, Dynamic IPv4 source guard using DHCP snooping configuration example,
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 240 highlights
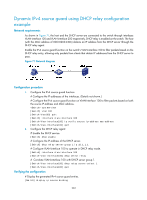
# Configure GigabitEthernet 1/0/2 to allow only IP packets with the source MAC address of 0001-0203-0406 and the source IP address of 192.168.0.1 to pass. [DeviceB] interface gigabitethernet 1/0/2 [DeviceB-GigabitEthernet1/0/2] ip source binding ip-address 192.168.0.1 mac-address 0001-0203-0406 [DeviceB-GigabitEthernet1/0/2] quit # Configure the IPv4 source guard function on GigabitEthernet 1/0/1 to filter packets based on the source IP address. [DeviceB] interface gigabitethernet 1/0/1 [DeviceB-GigabitEthernet1/0/1] ip verify source ip-address # Configure GigabitEthernet 1/0/1 to allow only IP packets with the source IP address of 192.168.0.2 to pass. [DeviceB-GigabitEthernet1/0/1] ip source binding ip-address 192.168.0.2 [DeviceB-GigabitEthernet1/0/1] quit Verifying the configuration # On Device A, display information about static IPv4 source guard entries. The output shows that the static IPv4 source guard entries are configured successfully. [DeviceA] display ip source binding static Total entries found: 2 MAC Address IP Address VLAN Interface Type 0001-0203-0405 192.168.0.3 N/A GE1/0/2 Static 0001-0203-0406 192.168.0.1 N/A GE1/0/1 Static # On Device B, display information about static IPv4 source guard entries. The output shows that the static IPv4 source guard entries are configured successfully. [DeviceB] display ip source binding static Total entries found: 2 MAC Address IP Address VLAN Interface Type 0001-0203-0406 192.168.0.1 N/A GE1/0/2 Static N/A 192.168.0.2 N/A GE1/0/1 Static Dynamic IPv4 source guard using DHCP snooping configuration example Network requirements As shown in Figure 70, the device connects to the host (client) and the DHCP server through ports GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2 respectively. The host obtains an IP address from the DHCP server. Enable DHCP snooping on the device to record the DHCP snooping entry of the host. Enable the IPv4 source guard function on the device's port GigabitEthernet 1/0/1 to filter packets based on the DHCP snooping entry, allowing only packets from clients that obtain IP addresses through the DHCP server to pass. For information about DHCP server configuration, see Layer 3-IP Services Configuration Guide. 230