HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 31
Specifying the RADIUS authentication/authorization servers
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 31 highlights
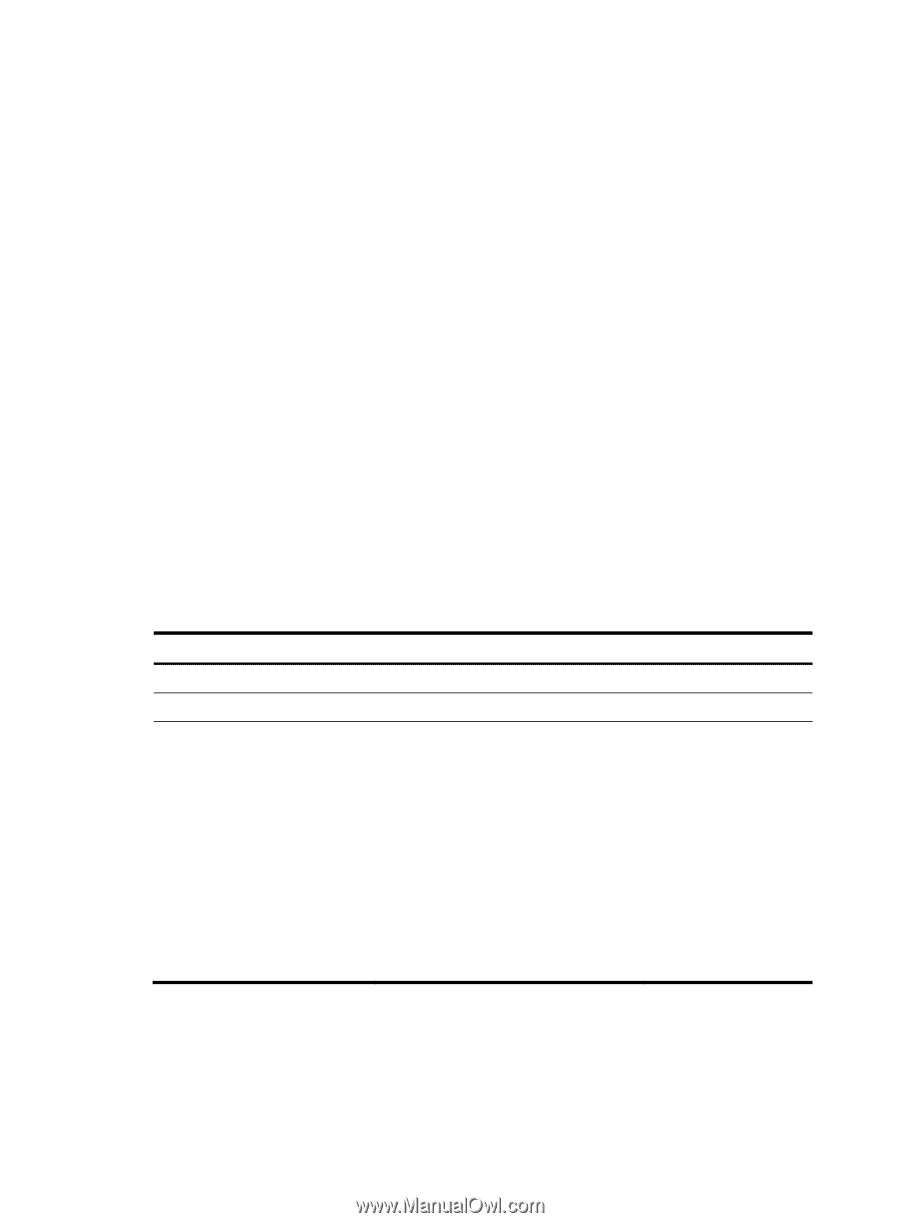
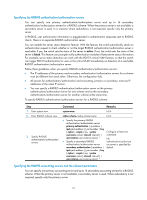
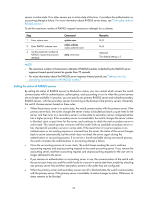
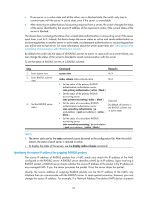
Specifying the RADIUS authentication/authorization servers You can specify one primary authentication/authorization server and up to 16 secondary authentication/authorization servers for a RADIUS scheme. When the primary server is not available, a secondary server is used. In a scenario where redundancy is not required, specify only the primary server. In RADIUS, user authorization information is piggybacked in authentication responses sent to RADIUS clients. There is no separate RADIUS authorization server. You can enable the server status detection feature. With the feature, the switch periodically sends an authentication request to check whether or not the target RADIUS authentication/authorization server is reachable. If yes, the switch sets the status of the server to active. If not, the switch sets the status of the server to block. This feature can promptly notify authentication modules of latest server status information. For example, server status detection can work with the 802.1X critical VLAN feature, so that the switch can trigger 802.1X authentication for users in the critical VLAN immediately on detection of a reachable RADIUS authentication/authorization server. Follow these guidelines when you specify RADIUS authentication/authorization servers: • The IP addresses of the primary and secondary authentication/authorization servers for a scheme must be different from each other. Otherwise, the configuration fails. • All servers for authentication/authorization and accounting, primary or secondary, must use IP addresses of the same IP version. • You can specify a RADIUS authentication/authorization server as the primary authentication/authorization server for one scheme and as the secondary authentication/authorization server for another scheme at the same time. To specify RADIUS authentication/authorization servers for a RADIUS scheme: Step 1. Enter system view. 2. Enter RADIUS scheme view. 3. Specify RADIUS authentication/authorization servers. Command Remarks system-view N/A radius scheme radius-scheme-name • Specify the primary RADIUS authentication/authorization server: primary authentication { ip-address | ipv6 ipv6-address } [ port-number | key [ cipher | simple ] key | probe username name [ interval interval ] | vpn-instance vpn-instance-name ] * • Specify a secondary RADIUS authentication/authorization server: secondary authentication { ip-address | ipv6 ipv6-address } [ port-number | key [ cipher | simple ] key | probe username name [ interval interval ] | vpn-instance vpn-instance-name ] * N/A Configure at least one command. No authentication/authorizat ion server is specified by default. Specifying the RADIUS accounting servers and the relevant parameters You can specify one primary accounting server and up to 16 secondary accounting servers for a RADIUS scheme. When the primary server is not available, a secondary server is used. When redundancy is not required, specify only the primary server. 21