HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 85
Guest VLAN, Layer 2, LAN Switching, Configuration Guide
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 85 highlights
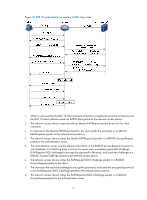
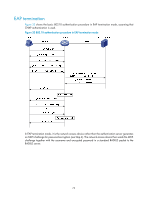
With 802.1X authentication, a hybrid port is always assigned to a VLAN as an untagged member. After the assignment, do not re-configure the port as a tagged member in the VLAN. On a periodic online user re-authentication enabled port, if a user has been online before you enable the MAC-based VLAN function, the access device does not create a MAC-to-VLAN mapping for the user unless the user passes re-authentication and the VLAN for the user has changed. Guest VLAN You can configure a guest VLAN on a port to accommodate users that have not performed 802.1X authentication, so they can access a limited set of network resources, such as a software server, to download anti-virus software and system patches. After a user in the guest VLAN passes 802.1X authentication, it is removed from the guest VLAN and can access authorized network resources. The way that the network access device handles VLANs on the port differs by 802.1X access control mode. For more information about VLAN configuration and MAC-based VLAN, see Layer 2-LAN Switching Configuration Guide. 1. On a port that performs port-based access control Authentication status VLAN manipulation No 802.1X user has performed authentication within 90 seconds after 802.1X is enabled Assigns the 802.1X guest VLAN to the port as the PVID. All 802.1X users on this port can access only resources in the guest VLAN. If no 802.1X guest VLAN is configured, the access device does not perform any VLAN operation. A user in the 802.1X guest VLAN fails 802.1X authentication A user in the 802.1X guest VLAN passes 802.1X authentication If an 802.1X Auth-Fail VLAN (see "Auth-Fail VLAN") is available, assigns the Auth-Fail VLAN to the port as the PVID. All users on this port can access only resources in the Auth-Fail VLAN. If no Auth-Fail VLAN is configured, the PVID on the port is still the 802.1X guest VLAN. All users on the port are in the guest VLAN. • Assigns the VLAN specified for the user to the port as the PVID, and removes the port from the 802.1X guest VLAN. After the user logs off, the user configured PVID restores. • If the authentication server assigns no VLAN, the user-configured PVID applies. The user and all subsequent 802.1X users are assigned to the user-configured port VLAN. After the user logs off, the PVID remains unchanged. 2. On a port that performs MAC-based access control To use the 802.1X guest VLAN function on a port that performs MAC-based access control, make sure that the port is a hybrid port, and enable MAC-based VLAN on the port. Authentication status VLAN manipulation A user has not passed 802.1X Creates a mapping between the MAC address of the user and the 802.1X authentication yet guest VLAN. The user can access resources in the guest VLAN. A user in the 802.1X guest VLAN fails 802.1X authentication If an 802.1X Auth-Fail VLAN is available, re-maps the MAC address of the user to the Auth-Fail VLAN. The user can access only resources in the Auth-Fail VLAN. If no 802.1X Auth-Fail VLAN is configured, the user is still in the 802.1X guest VLAN. 75