HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 25
Configuring AAA schemes, Configuring local users
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 25 highlights
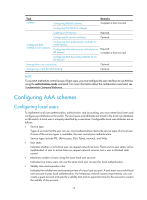
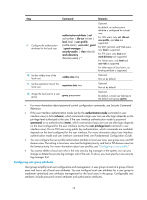
Task schemes Configuring RADIUS schemes Remarks Complete at least one task. Configuring HWTACACS schemes Creating an ISP domain Required. Configuring ISP domain attributes Optional. Configuring AAA methods for ISP domains Configuring AAA authentication methods for an ISP domain Configuring AAA authorization methods for an ISP domain Configuring AAA accounting methods for an ISP domain Required. Complete at least one task. Tearing down user connections Optional. Configuring a NAS ID-VLAN binding Optional. NOTE: To use AAA methods to control access of login users, you must configure the user interfaces to use AAA by using the authentication-mode command. For more information about the configuration command, see Fundamentals Command Reference. Configuring AAA schemes Configuring local users To implement local user authentication, authorization, and accounting, you must create local users and configure user attributes on the switch. The local users and attributes are stored in the local user database on the switch. A local user is uniquely identified by a username. Configurable local user attributes are as follows: • Service type: Types of services that the user can use. Local authentication checks the service types of a local user. If none of the service types is available, the user cannot pass authentication. Service types include FTP, LAN access, SSH, Telnet, terminal, and Web. • User state: Indicates whether or not a local user can request network services. There are two user states: active and blocked. A user in active state can request network services, but a user in blocked state cannot. • Maximum number of users using the same local user account: Indicates how many users can use the same local user account for local authentication. • Validity time and expiration time: Indicates the validity time and expiration time of a local user account. A user must use a valid local user account to pass local authentication. For temporary network access requirements, you can create a guest account and specify a validity time and an expiration time for the account to control the validity of the account. 15