HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 269
Configuring MFF, Overview
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 269 highlights
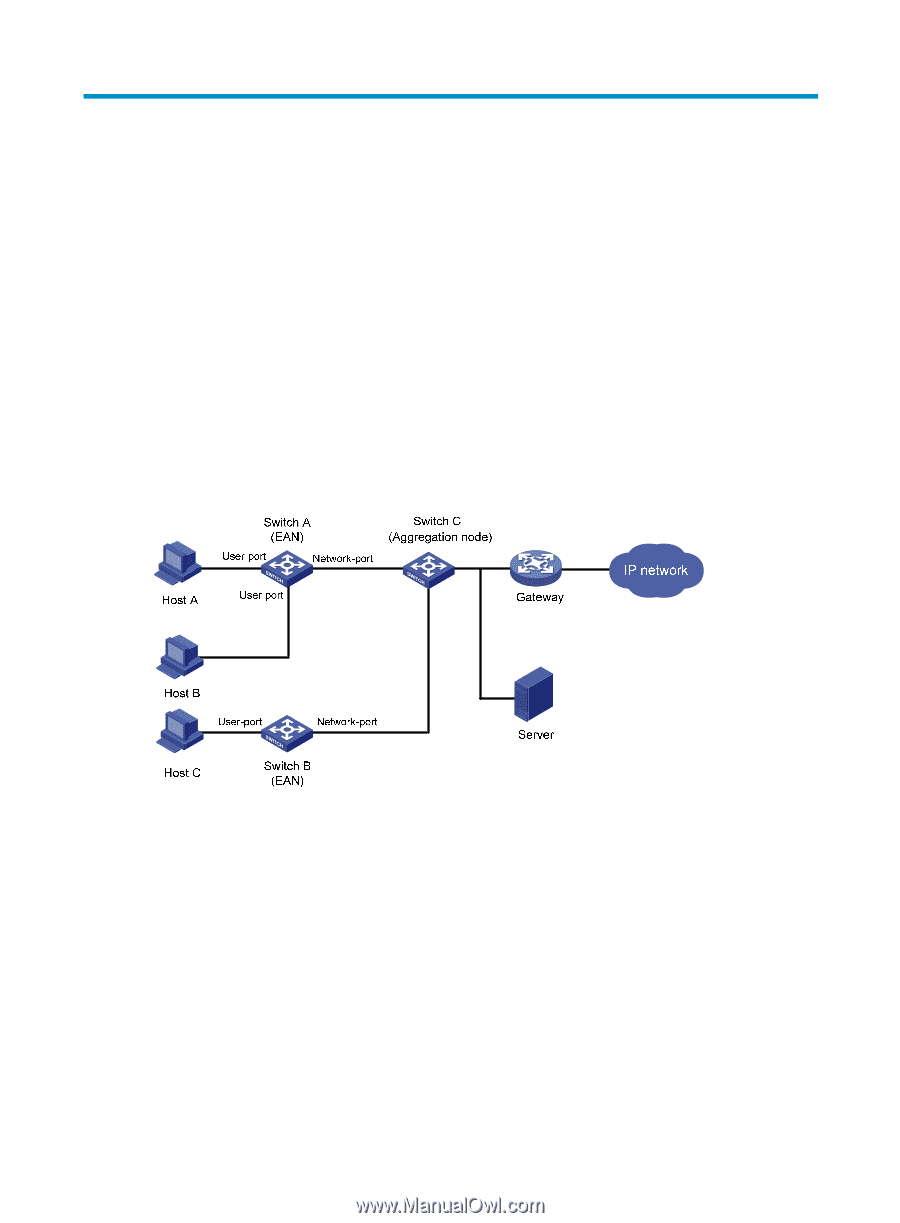
Configuring MFF Overview Traditional Ethernet networking solutions use the VLAN technology to isolate users at Layer 2 and to allow them to communicate at Layer 3. However, when a large number of hosts need to be isolated at Layer 2, many VLAN resources are occupied, and many IP addresses are used because you have to assign a network segment to each VLAN and an IP address to each VLAN interface for Layer 3 communication. MAC-forced forwarding (MFF) provides a solution for Layer 2 isolation and Layer 3 communication between hosts in the same broadcast domain. An MFF enabled device intercepts an ARP request and then returns the MAC address of a gateway (or server) to the sender. In this way, the sender is forced to send packets to the gateway for traffic monitoring and attack prevention. Figure 83 Network diagram for MFF As shown in Figure 83, hosts are connected to Switch C (aggregation node) through Switch A and Switch B (Ethernet access nodes, or EANs). The MFF enabled EANs forward packets from the hosts to the gateway for further forwarding. Thus, the hosts, isolated at Layer 2, can communicate at Layer 3 without knowing the MAC address of each other. MFF is often used in cooperation with the DHCP snooping, ARP snooping, IP source guard, ARP detection, and VLAN mapping features to enhance network security by implementing traffic filtering, Layer 2 isolation, and Layer 3 communication on the access switches. For information about DHCP snooping, see Layer 3-IP Services Configuration Guide. For information about ARP snooping, see Layer 3-IP Services Configuration Guide. For information about IP source guard, see "Configuring IP source guard.." For information about ARP detection, see "Configuring ARP attack protection." For information about VLAN mapping, see Layer 2-LAN Switching Configuration Guide. 259