HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 167
PKI architecture, PKI operation,
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 167 highlights
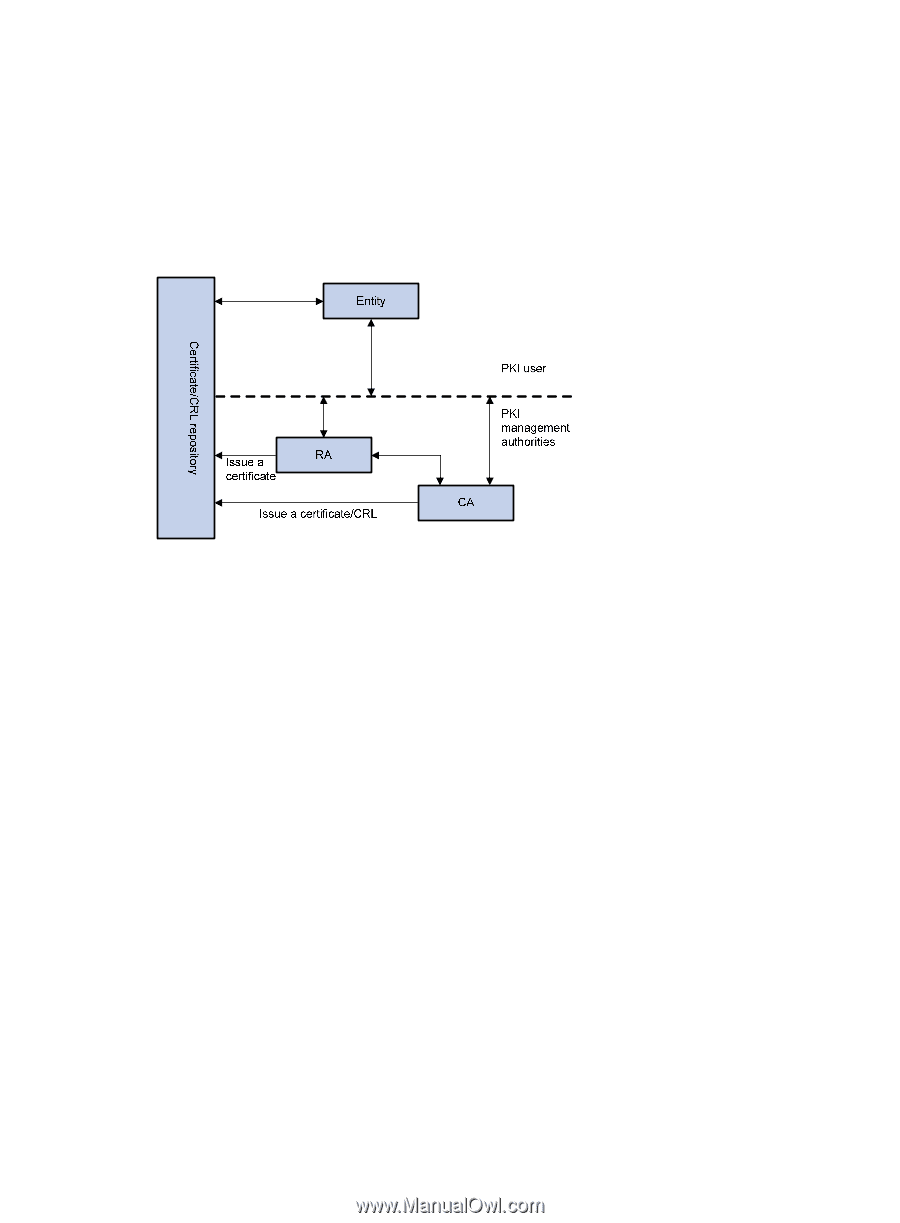
such as phone, disk, and email. As different CAs might use different methods to examine the binding of a public key with an entity, make sure that you understand the CA policy before selecting a trusted CA for certificate request. PKI architecture A PKI system consists of entities, a CA, a registration authority (RA) and a PKI repository. Figure 45 PKI architecture • Entity An entity is an end user of PKI products or services, such as a person, an organization, a device, or a process running on a computer. • CA A CA is a trusted authority responsible for issuing and managing digital certificates. A CA issues certificates, specifies the validity periods of certificates, and revokes certificates as needed by publishing CRLs. • RA A registration authority (RA) is an extended part of a CA or an independent authority. An RA can implement functions including identity authentication, CRL management, key pair generation and key pair backup. The PKI standard recommends that an independent RA be used for registration management to achieve higher security. • PKI repository A PKI repository can be a Lightweight Directory Access Protocol (LDAP) server or a common database. It stores and manages information like certificate requests, certificates, keys, CRLs and logs when it provides a simple query function. LDAP is a protocol for accessing and managing PKI information. An LDAP server stores user information and digital certificates from the RA server and provides directory navigation service. From an LDAP server, an entity can retrieve local and CA certificates of its own as well as certificates of other entities. PKI operation In a PKI-enabled network, an entity can request a local certificate from the CA and the device can check the validity of certificates. Here is how it operates: 157