HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 191
Configuration procedure, Enabling the SSH server function
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 191 highlights
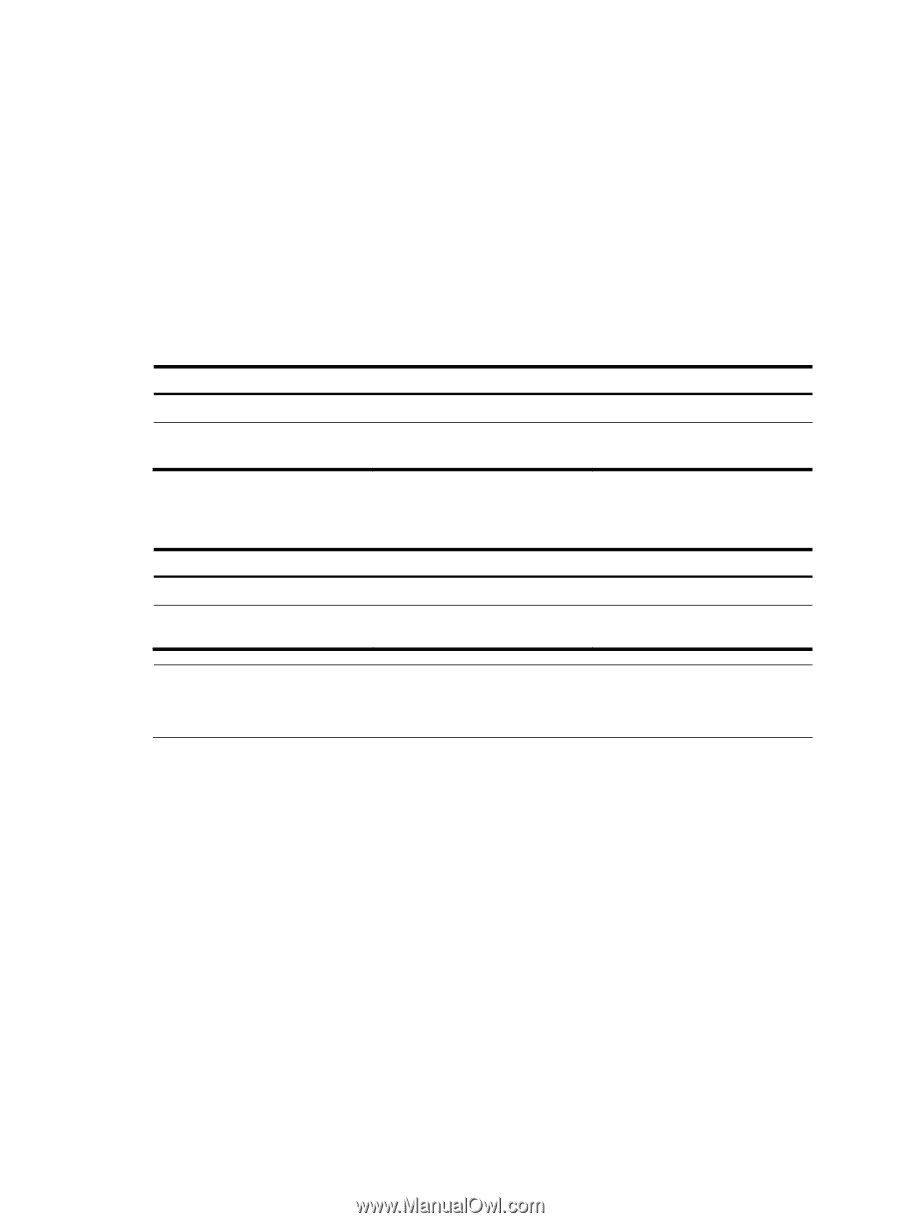
• The length of the modulus of RSA server keys and host keys must be in the range of 512 to 2048 bits. Some SSH2.0 clients require that the length of the key modulus be at least 768 bits on the SSH server side. • The public-key local create dsa command generates only the host key pair. SSH1 does not support the DSA algorithm. • The length of the modulus of DSA host keys must be in the range of 512 to 2048 bits. Some SSH2.0 clients require that the length of the key modulus be at least 768 bits on the SSH server side. • For more information about the public-key local create command, see Security Command Reference. Configuration procedure To generate DSA or RSA key pairs on the SSH server: Step 1. Enter system view. 2. Generate DSA or RSA key pairs. Command Remarks system-view N/A public-key local create { dsa | rsa } By default, neither DSA nor RSA key pairs exist. Enabling the SSH server function Step 1. Enter system view. 2. Enable the SSH server function. Command system-view ssh server enable Remarks N/A Disabled by default NOTE: When the device acts as an SCP server, only one SCP user is allowed to access to the SCP server at one time. Configuring the user interfaces for SSH clients An SSH client accesses the switch through a VTY user interface. You must configure the user interfaces for SSH clients to allow SSH login. The configuration takes effect only for clients that log in after the configuration. Configuration guidelines • If you configure a user interface to support SSH, be sure to configure the corresponding authentication mode with the authentication-mode scheme command. • For a user interface configured to support SSH, you cannot change the authentication mode. To change the authentication mode, undo the SSH support configuration first. Configuration procedure To configure the protocols for a user interface to support: 181